Security News > 2023 > June > Chinese UNC4841 Group Exploits Zero-Day Flaw in Barracuda Email Security Gateway
A suspected China-nexus threat actor dubbed UNC4841 has been linked to the exploitation of a recently patched zero-day flaw in Barracuda Email Security Gateway appliances since October 2022.
"UNC4841 is an espionage actor behind this wide-ranging campaign in support of the People's Republic of China," Google-owned Mandiant said in a new report published today, describing the group as "Aggressive and skilled."
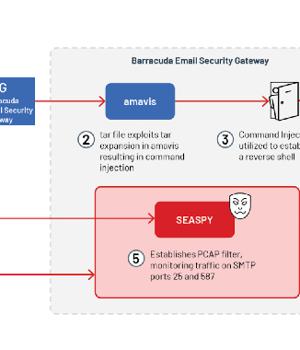
The flaw in question is CVE-2023-2868, which relates to a remote code injection affecting versions 5.1.3.001 through 9.2.0.006 that arises as a result of an incomplete validation of attachments contained within incoming emails.
Now according to the incident response and threat intelligence firm, which was appointed to probe the hack, UNC4841 is said to have sent emails to victim organizations containing malicious TAR file attachments that were designed to exploit the bug as early as October 10, 2022.
UNC4841 has all the hallmarks of a persistent actor, given its ability to swiftly alter its malware and employ additional persistence mechanisms as Barracuda initiated containment efforts after discovering the activity on May 19, 2023.
Data exfiltration entailed the capture of email related data in a subset of cases.
News URL
https://thehackernews.com/2023/06/chinese-unc4841-group-exploits-zero-day.html
Related news
- XE Hacker Group Exploits VeraCore Zero-Day to Deploy Persistent Web Shells (source)
- Chinese Hackers Exploit MAVInject.exe to Evade Detection in Targeted Cyber Attacks (source)
- ⚡ THN Weekly Recap: Alerts on Zero-Day Exploits, AI Breaches, and Crypto Heists (source)
- URGENT: Microsoft Patches 57 Security Flaws, Including 6 Actively Exploited Zero-Days (source)
- Patch Tuesday: Microsoft Fixes 57 Security Flaws – Including Active Zero-Days (source)
- Cybercriminals Exploit CSS to Evade Spam Filters and Track Email Users' Actions (source)
- APTs have been using zero-day Windows shortcut exploit for eight years (ZDI-CAN-25373) (source)
- Stealthy Apache Tomcat Critical Exploit Bypasses Security Filters: Are You at Risk? (source)
- Zero-Day Alert: Google Releases Chrome Patch for Exploit Used in Russian Espionage Attacks (source)
- EncryptHub Exploits Windows Zero-Day to Deploy Rhadamanthys and StealC Malware (source)
Related Vulnerability
| DATE | CVE | VULNERABILITY TITLE | RISK |
|---|---|---|---|
| 2023-05-24 | CVE-2023-2868 | Command Injection vulnerability in Barracuda products A remote command injection vulnerability exists in the Barracuda Email Security Gateway (appliance form factor only) product effecting versions 5.1.3.001-9.2.0.006. | 9.8 |