Security News > 2023 > May

In this article, we'll provide an overview of password cracking, discuss the importance of strong passwords, and detail the top 5 password cracking techniques hackers use. Whether you're a seasoned IT professional or just getting started, you need to understand these password cracking techniques to help better secure your organization's data.

Joseph James O'Connor, aka 'PlugwalkJoke,' has pleaded guilty to multiple cybercrime offenses, including SIM swapping attacks, cyberstalking, computer hacking, and hijacking high-profile accounts on Twitter and TikTok. O'Connor admitted his role in the hack that impacted Twitter in June 2020, where he and his three co-conspirators gained access to the accounts of high-profile individuals such as Barack Obama, Joe Biden, Elon Musk, Bill Gates, Jeff Bezos, Warren Buffet, Binance, Apple, Uber, and Bitcoin.
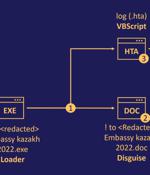
Government organizations in Central Asia are the target of a sophisticated espionage campaign that leverages a previously undocumented strain of malware dubbed DownEx. The Romanian cybersecurity firm said it first detected the malware in a highly targeted attack aimed at foreign government institutions in Kazakhstan in late 2022.

A 23-year-old British citizen has confessed to "Multiple schemes" involving computer crimes, including playing a part in the July 2020 Twitter attack that saw the accounts of Amazon CEO Jeff Bezos, Kanye West, and former President Barack Obama hijacked by an unidentified crew. The 2020 Twitter attack happened when blue ticks still meant "Verified account" and was accomplished using social engineering just as the COVID-19 pandemic was starting to gain traction.

In a new report by Cisco Talos, researchers explain how the Greatness phishing platform launched in mid-2022, with a spike in activity in December 2022 and then again in March 2023. The phishing service will automatically inject the target's company logo and background image from the employer's actual Microsoft 365 login page.

The US Government has been investigating Snake and Snake-related malware tools for nearly 20 years, and has monitored FSB officers assigned to Turla conducting daily operations using Snake from a known FSB facility in Ryazan, Russia. Although Snake has been the subject to several cybersecurity industry reports throughout its existence, Turla has applied numerous upgrades and revisions, and selectively deployed it, all to ensure that Snake remains Turla's most sophisticated long-term cyberespionage malware implant.

Once attackers interact with a honeypot, the system can collect information about the attack and the attacker's tactics, techniques, and procedures. To attract attackers, a honeypot needs to appear legitimate and isolated from the real production network, making them challenging to set up and scale for a blue team looking to develop intrusion detection capabilities.

GitHub is making push protection - a security feature designed to automatically prevent the leaking of secrets to repositories - free for owners of all public repositories. Prevent leaking secrets with GitHub push protection.

Britain's leaky outsourcing behemoth Capita is warning investors that the clean-up bill for its recent digital break-in will cost up to £20 million. At the end of March, the business was blindsided when criminals broke into its tech infrastructure and stayed inside for more than a week before Capita realized it was the victim of a "Cyber incident."

A U.K. national has pleaded guilty in connection with the July 2020 Twitter attack affecting numerous high-profile accounts and defrauding other users of the platform. Joseph James O'Connor, who also went by the online alias PlugwalkJoe, admitted to "His role in cyberstalking and multiple schemes that involve computer hacking, including the July 2020 hack of Twitter," the U.S. Department of Justice said.