Security News > 2023 > May > Hackers Using Golang Variant of Cobalt Strike to Target Apple macOS Systems
A Golang implementation of Cobalt Strike called Geacon is likely to garner the attention of threat actors looking to target Apple macOS systems.
Geacon is a Go variant of Cobalt Strike that has been available on GitHub since February 2020.
H4de5, the developer behind geacon pro, claims the tool is mainly designed to support CobaltStrike versions 4.1 and later, while geacon plus supports CobaltStrike version 4.0.
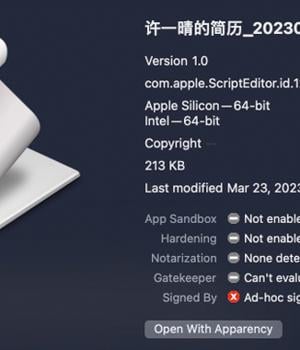
App, one of the artifacts discovered by SentinelOne, employs a run-only AppleScript to reach out to a remote server and download a Geacon payload. It's compatible with both Apple silicon and Intel architectures.
The Geacon binary, compiled from the geacon plus source code, packs a multitude of functions that allows it to download next-stage payloads and exfiltrate data, and facilitate network communications.
Its main component is a Geacon payload built from the geacon pro project that connects to a known command-and-control server in Japan.
News URL
https://thehackernews.com/2023/05/hackers-using-golang-variant-of-cobalt.html