Security News > 2023 > April
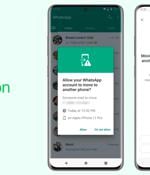
"Mobile device malware is one of the biggest threats to people's privacy and security today because it can take advantage of your phone without your permission and use your WhatsApp to send unwanted messages," the Meta-owned company said in an announcement. Called Device Verification, the security measure is designed to help prevent account takeover attacks by blocking the threat actor's connection and allowing the target to use the app without any interruption.

WhatsApp announced today the introduction of several new security features, one of them dubbed "Device Verification" and designed to provide better protection against account takeover attacks. Device Verification prevents malware from using authentication keys stolen from infected mobile devices or via unofficial clients to impersonate accounts and use them to send scam and phishing messages to people in the targeted users' contact lists.

Google has announced the Google Cloud Assured Open Source Software service, which aims to be a trusted source of secure open source packages, and the deps. With Assured OSS, Google offers organizations the opportunity to integrate into their own developer workflows the same OSS packages Google uses and secures.

Thieves cut through the wall of a coffee shop to get to an Apple store, bypassing the alarms in the process. My favorite example is a band of California art thieves that would break into people's houses by cutting a hole in their walls with a chainsaw.
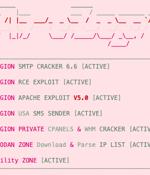
An emerging Python-based credential harvester and a hacking tool named Legion is being marketed via Telegram as a way for threat actors to break into various online services for further exploitation. The malware is suspected to be linked to another malware family called AndroxGh0st that was first documented by cloud security services providerLacework in December 2022.

The Transparent Tribe threat actor has been linked to a set of weaponized Microsoft Office documents in attacks targeting the Indian education sector using a continuously maintained piece of malware called Crimson RAT. While the suspected Pakistan-based threat group is known to target military and government entities in the country, the activities have since expanded to include the education vertical. Last month, ESET attributed Transparent Tribe to a cyber espionage campaign aimed at infecting Indian and Pakistani Android users with a backdoor called CapraRAT. An analysis of Crimson RAT samples has revealed the presence of the word "Wibemax," corroborating a previous report from Fortinet.

To help you get started, I'll explore how APIs become hidden and discuss how shadow APIs can be used for malicious purposes. "Do you know how many APIs you have? Better yet, do you know if your APIs are exposing sensitive data? If you're struggling with shadow APIs in your environment, you should download the Definitive Guide to API Discovery from Noname Security. Learn how to find and fix all your APIs - no matter the type."

To combat the surge of fake LinkedIn accounts in recent years, Microsoft has introduced Entra Verified ID, a new feature that allows users to verify their workplace on the business-focused social media platform. "As the credential holder, the employee can decide to share their credential with apps and websites, such as LinkedIn. Then the verifier can cryptographically authenticate that the digital employee ID is genuine and was issued by the place of work the employee claims. This approach represents a more secure, convenient, and trustworthy way to verify digital information at scale."

Apart from extracting credentials and breaching web services, Legion can also create administrator users, implant webshells, and send out spam SMS to customers of U.S. carriers. The tool uses an array of methods to retrieve credentials from misconfigured web servers, like targeting environment variable files and configuration files that might contain SMTP, AWS console, Mailgun, Twilio, and Nexmo credentials.
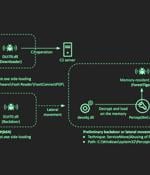
The North Korean threat actor known as the Lazarus Group has been observed shifting its focus and rapidly evolving its tools and tactics as part of a long-running activity called DeathNote. The targeting of the automotive and academic verticals is tied to Lazarus Group's broader attacks against the defense industry, as documented by the Russian cybersecurity firm in October 2021, leading to the deployment of BLINDINGCAN and COPPERHEDGE implants.