Security News > 2023 > April > Hackers Using Self-Extracting Archives Exploit for Stealthy Backdoor Attacks
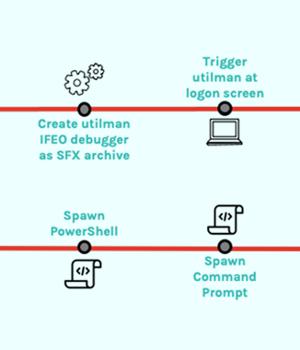
An unknown threat actor used a malicious self-extracting archive file in an attempt to establish persistent backdoor access to a victim's environment, new findings from CrowdStrike show.
SFX files are capable of extracting the data contained within them without the need for dedicated software to display the file contents.
"Closer inspection of the SFX archive revealed that it functions as a password-protected backdoor by abusing WinRAR setup options rather than containing any malware," Minton explained.
Specifically, the file is engineered to run PowerShell, Command Prompt, and Task Manager with NT AUTHORITYSYSTEM privileges by providing the right password to the archive.
A month later, the infamous Emotet botnet was observed sending out an SFX archive that, once opened by a user, would automatically extract a second password-protected SFX archive, enter the password, and execute its content without further user interaction using a batch script.
To mitigate threats posed by this attack vector, it's recommended that SFX archives are analyzed through unarchiving software to identify any potential scripts or binaries that are set to extract and run upon execution.
News URL
https://thehackernews.com/2023/04/hackers-using-self-extracting-archives.html
Related news
- New ‘Rules File Backdoor’ Attack Lets Hackers Inject Malicious Code via AI Code Editors (source)
- Hackers Exploit Severe PHP Flaw to Deploy Quasar RAT and XMRig Miners (source)
- TechRepublic EXCLUSIVE: New Ransomware Attacks are Getting More Personal as Hackers ‘Apply Psychological Pressure” (source)
- Ongoing Cyber Attacks Exploit Critical Vulnerabilities in Cisco Smart Licensing Utility (source)
- Zero-Day Alert: Google Releases Chrome Patch for Exploit Used in Russian Espionage Attacks (source)
- New npm attack poisons local packages with backdoors (source)
- New SparrowDoor Backdoor Variants Found in Attacks on U.S. and Mexican Organizations (source)
- Top 3 MS Office Exploits Hackers Use in 2025 – Stay Alert! (source)
- Hackers Repurpose RansomHub's EDRKillShifter in Medusa, BianLian, and Play Attacks (source)
- Chinese FamousSparrow hackers deploy upgraded malware in attacks (source)