Security News > 2023 > March > AlienFox Malware Targets API Keys and Secrets from AWS, Google, and Microsoft Cloud Services
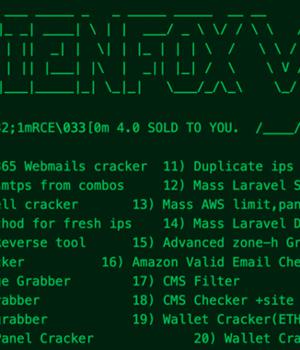
A new "Comprehensive toolset" called AlienFox is being distributed on Telegram as a way for threat actors to harvest credentials from API keys and secrets from popular cloud service providers.
"The spread of AlienFox represents an unreported trend towards attacking more minimal cloud services, unsuitable for crypto mining, in order to enable and expand subsequent campaigns," SentinelOne security researcher Alex Delamotte said in a report shared with The Hacker News.
The primary use of AlienFox is to enumerate misconfigured hosts via scanning platforms like LeakIX and SecurityTrails, and subsequently leverage various scripts in the toolkit to extract credentials from configuration files exposed on the servers.
Recent versions of the tool incorporate the ability to establish persistence on an Amazon Web Services account and escalate privileges as well as automate spam campaigns through the compromised accounts.
Attacks involving AlienFox are said to be opportunistic, with the scripts capable of gathering sensitive data pertaining to AWS, Bluemail, Exotel, Google Workspace, Mailgun, Mandrill, Microsoft 365, Sendgrid, Twilio, Zimbra, and Zoho.
"The AlienFox toolset demonstrates another stage in the evolution of cybercrime in the cloud," Delamotte said.
News URL
https://thehackernews.com/2023/03/alienfox-malware-targets-api-keys-and.html
Related news
- Google's got a hot cloud infosec startup, a new unified platform — and its eye on Microsoft's $20B+ security biz (source)
- Microsoft Teams tactics, malware connect Black Basta, Cactus ransomware (source)
- Microsoft admits GitHub hosted malware that infected almost a million devices (source)
- Microsoft: New RAT malware used for crypto theft, reconnaissance (source)
- Google Acquires Wiz for $32 Billion in Its Biggest Deal Ever to Boost Cloud Security (source)
- Google to purchase Wiz for $32 billion in cloud security play (source)
- Microsoft Trust Signing service abused to code-sign malware (source)
- Microsoft Trusted Signing service abused to code-sign malware (source)
- New Android malware uses Microsoft’s .NET MAUI to evade detection (source)
- Android Malware Exploits a Microsoft-Related Security Blind Spot to Avoid Detection (source)