Security News > 2023 > January

Within a few weeks of ChatGPT going live, participants in cybercrime forums-some with little or no coding experience-were using it to write software and emails that could be used for espionage, ransomware, malicious spam, and other malicious tasks.The Python code combined various cryptographic functions, including code signing, encryption, and decryption.

When a client's server goes down or is compromised in a cyberattack, managed service providers need an effective business continuity and disaster recovery solution to restore data and operations quickly, without sacrificing margin. That means industry-leading recovery technology from a vendor that is there to support you, no matter what.

We and our store and/or access information on a device, such as cookies and process personal data, such as unique identifiers and standard information sent by a device for personalised ads and content, ad and content measurement, and audience insights, as well as to develop and improve products. With your permission we and our partners may use precise geolocation data and identification through device scanning.

SIRIS is fundamentally different than traditional backup and recovery solutions. Utilizing a cloud-first approach, managed service providers can offer their clients an all-in-one solution that incorporates local backup and recovery with a secure, cloud-based repository and full disaster recovery in the cloud.

Security veteran Chris Deibler, the new VP of Security at DataGrail, has been brought in to build the company's security team to support its growth. A former Director of Security Engineering at Shopify and Director of Security at Twitch, he knows a thing or two about successfully instituting a security organization within an enterprise, so we decided to pick his brain on the subject.
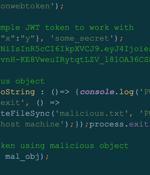
A high-severity security flaw has been disclosed in the open source jsonwebtoken library that, if successfully exploited, could lead to remote code execution on a target server. "By exploiting this vulnerability, attackers could achieve remote code execution on a server verifying a maliciously crafted JSON web token request," Palo Alto Networks Unit 42 researcher Artur Oleyarsh said in a Monday report.

A strong identity governance strategy can address these hurdles, and should be a foundational part of every IT and security initiative. Today, even organizations with the most modern IT frameworks are looking for a way to orchestrate identity management across hybrid-cloud environments.

In this Help Net Security video, Karthik Kannan, CEO at Anvilogic, talks about predictions for the cybersecurity world in 2023 and how to gain security consciousness through cost. The post How to...

Compliance services are emerging as one of the hottest areas of cybersecurity. As large businesses adopt cybersecurity and compliance frameworks and agree to certain standards, they impose similar demands on their suppliers.

Pakistan's government has warned its agencies that the dark web exists, is home to all sorts of unpleasant people, and should be avoided. Linking the dark web to terrorism therefore associates the networks with threats to national security.