Security News > 2022 > October > Hackers Can Use 'App Mode' in Chromium Browsers' for Stealth Phishing Attacks
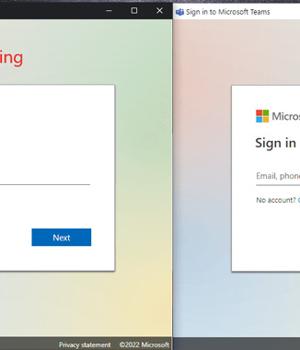
In what's a new phishing technique, it has been demonstrated that the Application Mode feature in Chromium-based web browsers can be abused to create "Realistic desktop phishing applications."
Application Mode is designed to offer native-like experiences in a manner that causes the website to be launched in a separate browser window, while also displaying the website's favicon and hiding the address bar.
"Although this technique is meant more towards internal phishing, you can technically still use it in an external phishing scenario," mr.
This is achieved by setting up a phishing page with a fake address bar at the top, and configuring the -app parameter to point to the phishing site hosting the page.
On top of that, the attacker-controlled phishing site can make use of JavaScript to take more actions, such as closing the window immediately after the user enters the credentials or resizing and positioning it to achieve the desired effect.
The findings come as new findings Trustwave SpiderLabs show that HTML smuggling attacks are a common occurrence, with.
News URL
https://thehackernews.com/2022/10/hackers-can-use-app-mode-in-chromium.html
Related news
- Three Reasons Why the Browser is Best for Stopping Phishing Attacks (source)
- DPRK Hackers Steal $137M from TRON Users in Single-Day Phishing Attack (source)
- Hackers Repurpose RansomHub's EDRKillShifter in Medusa, BianLian, and Play Attacks (source)
- Chinese FamousSparrow hackers deploy upgraded malware in attacks (source)
- North Korean hackers adopt ClickFix attacks to target crypto firms (source)
- Phishing platform 'Lucid' behind wave of iOS, Android SMS attacks (source)
- Russian hackers attack Western military mission using malicious drive (source)
- iOS devices face twice the phishing attacks of Android (source)
- Browser extensions make nearly every employee a potential attack vector (source)
- Windows NTLM hash leak flaw exploited in phishing attacks on governments (source)