Security News > 2022 > September > North Korean Hackers Weaponizing Open-Source Software in Latest Cyber Attacks
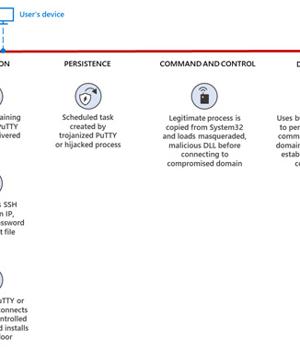
A "Highly operational, destructive, and sophisticated nation-state activity group" with ties to North Korea has been weaponizing open source software in their social engineering campaigns aimed at companies around the world since June 2022.
Attacks targeted employees in organizations across multiple industries, including media, defense and aerospace, and IT services in the U.S., the U.K., India, and Russia.
The tech giant said it observed Zinc leveraging a "Wide range of open-source software including PuTTY, KiTTY, TightVNC, Sumatra PDF Reader, and muPDF/Subliminal Recording software installer for these attacks."
According to CrowdStrike, Zinc "Has been active since 2009 in operations aimed at collecting political, military, and economic intelligence on North Korea's foreign adversaries and conducting currency generation campaigns."
"Zinc attacks appear to be motivated by traditional cyberespionage, theft of personal and corporate data, financial gain, and corporate network destruction," the company said.
"Zinc attacks bear many hallmarks of state-sponsored activities, such as heightened operational security, sophisticated malware that evolves over time, and politically motivated targeting."
News URL
https://thehackernews.com/2022/09/north-korean-hackers-weaponizing-open.html
Related news
- North Korean hackers adopt ClickFix attacks to target crypto firms (source)
- Hackers Repurpose RansomHub's EDRKillShifter in Medusa, BianLian, and Play Attacks (source)
- Chinese FamousSparrow hackers deploy upgraded malware in attacks (source)
- Open-source malware doubles, data exfiltration attacks dominate (source)
- North Korean Hackers Disguised as IT Workers Targeting UK, European Companies, Google Finds (source)
- North Korean Hackers Deploy BeaverTail Malware via 11 Malicious npm Packages (source)
- Russian hackers attack Western military mission using malicious drive (source)
- Hackers Abuse Russian Bulletproof Host Proton66 for Global Attacks and Malware Delivery (source)
- Hackers abuse Zoom remote control feature for crypto-theft attacks (source)
- DPRK Hackers Steal $137M from TRON Users in Single-Day Phishing Attack (source)