Security News > 2022 > September > Hackers Targeting Unpatched Atlassian Confluence Servers to Deploy Crypto Miners
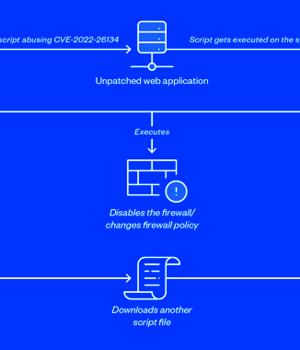
A now-patched critical security flaw affecting Atlassian Confluence Server that came to light a few months ago is being actively exploited for illicit cryptocurrency mining on unpatched installations.
In one of the infection chains observed by the cybersecurity company, the flaw was leveraged to download and run a shell script on the victim's machine, which, in turn, fetched a second shell script.
The malicious code is designed to update the PATH variable to include additional paths such as "/tmp", download the cURL utility from a remote server, disable iptables firewall, abuse the PwnKit flaw to gain root privileges, and ultimately deploy the hezb crypto miner.
Like other cryptojacking attacks, the shell script also terminates other competing coin miners, disables cloud service provider agents from Alibaba and Tencent, before carrying out lateral movement via SSH. The findings mirror similar exploitation attempts previously disclosed by Lacework, Microsoft, Sophos, and Akamai in June.
Lacework's analysis further shows that the command-and-control server used to retrieve the cURL software as well as the hezb miner also distributed a Golang-based ELF binary named "Kik" that enables the malware to kill processes of interest.
"Attackers could take advantage of injecting their own code for interpretation and gain access to the Confluence domain being targeted, as well as conduct attacks ranging from controlling the server for subsequent malicious activities to damaging the infrastructure itself," Bharti said.
News URL
https://thehackernews.com/2022/09/hackers-targeting-unpatched-atlassian.html
Related news
- North Korean hackers adopt ClickFix attacks to target crypto firms (source)
- Hackers abuse Zoom remote control feature for crypto-theft attacks (source)
- ASUS releases fix for AMI bug that lets hackers brick servers (source)
- North Korean Hackers Spread Malware via Fake Crypto Firms and Job Interview Lures (source)
- Hackers Exploit Critical Craft CMS Flaws; Hundreds of Servers Likely Compromised (source)
- Chinese hackers behind attacks targeting SAP NetWeaver servers (source)
- Türkiye Hackers Exploited Output Messenger Zero-Day to Drop Golang Backdoors on Kurdish Servers (source)
- Russia-linked hackers target webmail servers in Ukraine-related espionage operation (source)