Security News > 2022 > August > North Korean Hackers Using Malicious Browser Extension to Spy on Email Accounts
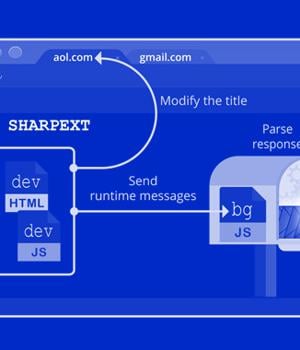
A threat actor operating with interests aligned with North Korea has been deploying a malicious extension on Chromium-based web browsers that's capable of stealing email content from Gmail and AOL. Cybersecurity firm Volexity attributed the malware to an activity cluster it calls SharpTongue, which is said to share overlaps with an adversarial collective publicly referred to under the name Kimsuky.
SharpTongue has a history of singling out individuals working for organizations in the U.S., Europe, and South Korea who "Work on topics involving North Korea, nuclear issues, weapons systems, and other matters of strategic interest to North Korea," researchers Paul Rascagneres and Thomas Lancaster said.
In 2018, the actor was seening a Chrome plugin as part of a campaign called Stolen Pencil to infect victims and steal browser cookies and passwords.
"This is the first time Volexity has observed malicious browser extensions used as part of the post-exploitation phase of a compromise," the researchers said.
"By stealing email data in the context of a user's already-logged-in session, the attack is hidden from the email provider, making detection very challenging."
While the tactics and tools used in the intrusions point to a North Korean hacking group called APT37, evidence gathered pertaining to the attack infrastructure suggests the involvement of the Russia-aligned APT28 actor.
News URL
https://thehackernews.com/2022/07/north-korean-hackers-using-malicious.html
Related news
- Russian Hackers Exploit Email and VPN Vulnerabilities to Spy on Ukraine Aid Logistics (source)
- North Korean hackers adopt ClickFix attacks to target crypto firms (source)
- North Korean Hackers Disguised as IT Workers Targeting UK, European Companies, Google Finds (source)
- North Korean Hackers Deploy BeaverTail Malware via 11 Malicious npm Packages (source)
- Cybersecurity firm buying hacker forum accounts to spy on cybercriminals (source)
- North Korean Hackers Spread Malware via Fake Crypto Firms and Job Interview Lures (source)
- Hackers Use Fake VPN and Browser NSIS Installers to Deliver Winos 4.0 Malware (source)