Security News > 2022 > April > New Nimbuspwn Linux vulnerability gives hackers root privileges
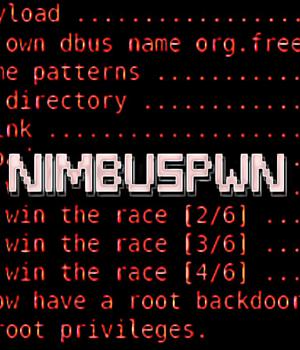
A new set of vulnerabilities collectively tracked as Nimbuspwn could let local attackers escalate privileges on Linux systems to deploy malware ranging from backdoors to ransomware.
Security researchers at Microsoft disclosed the issues in a report today noting that they can be chained together to achieve root privileges on a vulnerable system.
Tracked as CVE-2022-29799 and CVE-2022-29800, the Nimbuspwn security issues were discovered in networkd-dispatcher, a component that sends connection status changes on Linux machines.
One observation that piqued interest was that the networkd-dispatcher daemon was running at boot time with root privileges on the system.
The logic implemented by " run hooks for state" includes returning executable script files owned by the root user and the root group that are in the "/etc/networkd-dispatcher/.
An attacker can abuse this vulnerability to replace scripts that networkd-dispatcher believes to be owned by root to ones that are not.
News URL
Related Vulnerability
| DATE | CVE | VULNERABILITY TITLE | RISK |
|---|---|---|---|
| 2022-09-21 | CVE-2022-29800 | Time-of-check Time-of-use (TOCTOU) Race Condition vulnerability in Microsoft Windows Defender for Endpoint A time-of-check-time-of-use (TOCTOU) race condition vulnerability was found in networkd-dispatcher. | 4.7 |
| 2022-09-21 | CVE-2022-29799 | Path Traversal vulnerability in Microsoft Windows Defender for Endpoint A vulnerability was found in networkd-dispatcher. | 5.5 |