Security News > 2022 > March > SharkBot Banking Malware Spreading via Fake Android Antivirus App on Google Play Store
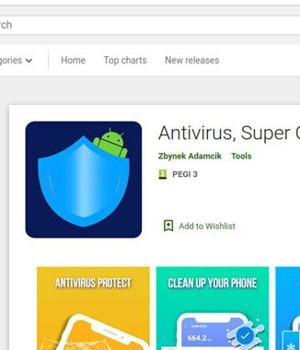
The threat actor behind a nascent Android banking trojan named SharkBot has managed to evade Google Play Store security barriers by masquerading as an antivirus app.
Where SharkBot stands apart is in its ability to carry out the unauthorized transactions via Automatic Transfer Systems, which stands in contrast to TeaBot, which requires a live operator to interact with the infected devices to conduct the malicious activities.
"The ATS features allow the malware to receive a list of events to be simulated, and they will be simulated in order to do the money transfers," Alberto Segura and Rolf Govers, malware analysts at cybersecurity firm NCC Group, said in a report published last week.
The latest version spotted on the Google Play Store on February 28 are a number of dropper apps that also leverages Android's Direct Reply functionality to propagate itself to other devices, making it the second banking trojan after FluBot to intercept notifications for wormable attacks.
SharkBot is also feature-rich in that it enables the adversary to inject fraudulent overlays atop official banking apps to steal credentials, log keystrokes, and obtain full remote control over the devices, but only after the victims grant it Accessibility Services permissions.
The findings come a week after researchers from Cleafy disclosed details of a new TeaBot variant found in the Play Store that's designed to target users of more than 400 banking and financial apps, including those from Russia, China, and the U.S..
News URL
https://thehackernews.com/2022/03/sharkbot-banking-malware-spreading-via.html
Related news
- APT36 Spoofs India Post Website to Infect Windows and Android Users with Malware (source)
- Android Malware Exploits a Microsoft-Related Security Blind Spot to Avoid Detection (source)
- New Android Trojan Crocodilus Abuses Accessibility to Steal Banking and Crypto Credentials (source)
- New Crocodilus malware steals Android users’ crypto wallet keys (source)
- Counterfeit Android devices found preloaded With Triada malware (source)
- Triada Malware Preloaded on Counterfeit Android Phones Infects 2,600+ Devices (source)
- Google fixes Android zero-days exploited in attacks, 60 other flaws (source)
- Google Releases Android Update to Patch Two Actively Exploited Vulnerabilities (source)
- SpyNote, BadBazaar, MOONSHINE Malware Target Android and iOS Users via Fake Apps (source)
- Google adds Android auto-reboot to block forensic data extractions (source)