Security News > 2022 > January > North Korean Hackers Using Windows Update Service to Infect PCs with Malware
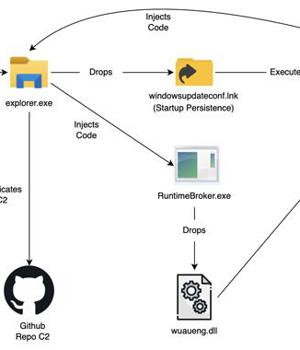
The notorious Lazarus Group actor has been observed mounting a new campaign that makes use of the Windows Update service to execute its malicious payload, expanding the arsenal of living-off-the-land techniques leveraged by the APT group to further its objectives.
The Lazarus Group, also known as APT38, Hidden Cobra, Whois Hacking Team, and Zinc, is the moniker assigned to the North Korea-based nation-state hacking group that's been active since at least 2009.
Last year, the threat actor was linked to an elaborate social engineering campaign targeting security researchers.
In the next phase, one of the loaded binaries, "Drops lnk.dll," leverages the Windows Update client to run a second module called "Wuaueng.dll." "This is an interesting technique used by Lazarus to run its malicious DLL using the Windows Update Client to bypass security detection mechanisms," researchers Ankur Saini and Hossein Jazi noted.
"Lazarus APT is one of the advanced APT groups that is known to target the defense industry," the researchers concluded.
"The group keeps updating its toolset to evade security mechanisms. Even though they have used their old job theme method, they employed several new techniques to bypass detections."
News URL
https://thehackernews.com/2022/01/north-korean-hackers-using-windows.html
Related news
- North Korean Hackers Deploy BeaverTail Malware via 11 Malicious npm Packages (source)
- North Korean Hackers Spread Malware via Fake Crypto Firms and Job Interview Lures (source)
- North Korean hackers adopt ClickFix attacks to target crypto firms (source)
- North Korean Hackers Disguised as IT Workers Targeting UK, European Companies, Google Finds (source)
- Microsoft Credits EncryptHub, Hacker Behind 618+ Breaches, for Disclosing Windows Flaws (source)
- WhatsApp vulnerability could be used to infect Windows users with malware (CVE-2025-30401) (source)
- Chinese Hackers Target Linux Systems Using SNOWLIGHT Malware and VShell Tool (source)
- State-Sponsored Hackers Weaponize ClickFix Tactic in Targeted Malware Campaigns (source)
- Chinese hackers target Russian govt with upgraded RAT malware (source)
- Hackers Abuse Russian Bulletproof Host Proton66 for Global Attacks and Malware Delivery (source)