Security News > 2022 > January > Hackers Using New Evasive Technique to Deliver AsyncRAT Malware
A new, sophisticated phishing attack has been observed delivering the AsyncRAT trojan as part of a malware campaign that's believed to have commenced in September 2021.
"Through a simple email phishing tactic with an html attachment, threat attackers are delivering AsyncRAT designed to remotely monitor and control its infected computers through a secure, encrypted connection," Michael Dereviashkin, security researcher at enterprise breach prevention firm Morphisec, said in a report.
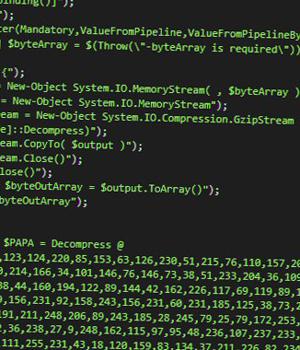
Opening the decoy file redirects the message recipient to a web page prompting the user to save an ISO file.
"The ISO download is not generated from a remote server but from within the victim's browser by a JavaScript code that's embedded inside the HTML receipt file," Dereviashkin explained.
This results in the execution of a.NET module in-memory that subsequently acts as a dropper for three files - one acting as a trigger for the next - to finally deliver AsyncRAT as the final payload, while also checking for antivirus software and setting up Windows Defender exclusions.
RATs such as AsyncRAT are typically used to forge a remote link between a threat actor and a victim device, steal information, and conduct surveillance through microphones and cameras.
News URL
https://thehackernews.com/2022/01/hackers-using-new-evasive-technique-to.html
Related news
- North Korean Hackers Deploy BeaverTail Malware via 11 Malicious npm Packages (source)
- Chinese Hackers Target Linux Systems Using SNOWLIGHT Malware and VShell Tool (source)
- State-Sponsored Hackers Weaponize ClickFix Tactic in Targeted Malware Campaigns (source)
- Chinese hackers target Russian govt with upgraded RAT malware (source)
- Hackers Abuse Russian Bulletproof Host Proton66 for Global Attacks and Malware Delivery (source)
- Iran-Linked Hackers Target Israel with MURKYTOUR Malware via Fake Job Campaign (source)
- North Korean Hackers Spread Malware via Fake Crypto Firms and Job Interview Lures (source)
- Iranian Hackers Maintain 2-Year Access to Middle East CNI via VPN Flaws and Malware (source)
- Russian Hackers Using ClickFix Fake CAPTCHA to Deploy New LOSTKEYS Malware (source)
- Hackers Use TikTok Videos to Distribute Vidar and StealC Malware via ClickFix Technique (source)