Security News > 2022 > January > Molerats Hackers Hiding New Espionage Attacks Behind Public Cloud Infrastructure
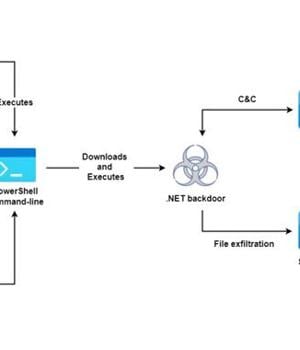
An active espionage campaign has been attributed to the threat actor known as Molerats that abuses legitimate cloud services like Google Drive and Dropbox to host malware payloads and for command-and-control and the exfiltration of data from targets across the Middle East.
The cyber offensive is believed to have been underway since at least July 2021, according to cloud-based information security company Zscaler, continuing previous efforts by the hacking group to conduct reconnaissance on the target hosts and plunder sensitive information.
Molerats, also tracked as TA402, Gaza Hackers Team, and Extreme Jackal, is an advanced persistent threat group that's largely focused on entities operating in the Middle East.
Attack activity associated with the actor has leveraged geopolitical and military themes to entice users to open Microsoft Office attachments and click on malicious links.
Investigating the attack infrastructure, the researchers said they found at least five Dropbox accounts used for this purpose.
"The targets in this campaign were chosen specifically by the threat actor and they included critical members of banking sector in Palestine, people related to Palestinian political parties, as well as human rights activists and journalists in Turkey," Zscaler ThreatLabz researchers Sahil Antil and Sudeep Singh said.
News URL
https://thehackernews.com/2022/01/molerats-hackers-hiding-new-espionage.html
Related news
- Russian hackers attack Western military mission using malicious drive (source)
- Hackers Abuse Russian Bulletproof Host Proton66 for Global Attacks and Malware Delivery (source)
- Hackers abuse Zoom remote control feature for crypto-theft attacks (source)
- DPRK Hackers Steal $137M from TRON Users in Single-Day Phishing Attack (source)
- Lazarus hackers breach six companies in watering hole attacks (source)
- SentinelOne Uncovers Chinese Espionage Campaign Targeting Its Infrastructure and Clients (source)
- Chinese Hackers Abuse IPv6 SLAAC for AitM Attacks via Spellbinder Lateral Movement Tool (source)
- CISA warns of hackers targeting critical oil infrastructure (source)
- Chinese hackers behind attacks targeting SAP NetWeaver servers (source)
- Output Messenger flaw exploited as zero-day in espionage attacks (source)