Security News > 2021 > October > New Attack Lets Hackers Collect and Spoof Browser's Digital Fingerprints
A "Potentially devastating and hard-to-detect threat" could be abused by attackers to collect users' browser fingerprinting information with the goal of spoofing the victims without their knowledge, thus effectively compromising their privacy.
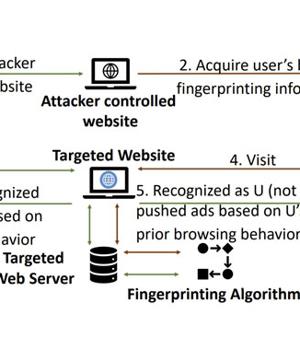
Academics from Texas A&M University dubbed the attack system "Gummy Browsers," likening it to a nearly 20-year-old "Gummy Fingers" technique that can impersonate a user's fingerprint biometrics.
"Then, orchestrates a browser on his own machine to replicate and transmit the same fingerprinting information when connecting to ????, fooling to think that is the one requesting the service rather than ????.".
Browser fingerprinting, also called machine fingerprinting, refers to a tracking technique that's used to uniquely identify internet users by gathering attributes about the software and hardware of a remote computing system - such as the choice of browser, timezone, default language, screen resolution, add-ons, installed fonts, and even preferences - as well as behavioral characteristics that emerge when interacting with the web browser of the device.
Thus in the event the website populates targeted ads based on only the users' browser fingerprints, it could result in a scenario where the remote adversary can profile any target of interest by manipulating their own fingerprints to match that of the victim for extended periods of time, all the while the user and the website remain oblivious to the attack.
In experimental tests, the researchers found that the attack system achieved average false-positive rates of greater than 0.95, indicating that most of the spoofed fingerprints were misrecognized as legitimate ones, thereby successfully tricking the digital fingerprinting algorithms.
News URL
Related news
- Russian hackers attack Western military mission using malicious drive (source)
- Browser extensions make nearly every employee a potential attack vector (source)
- Hackers Abuse Russian Bulletproof Host Proton66 for Global Attacks and Malware Delivery (source)
- Hackers abuse Zoom remote control feature for crypto-theft attacks (source)
- Three Reasons Why the Browser is Best for Stopping Phishing Attacks (source)
- DPRK Hackers Steal $137M from TRON Users in Single-Day Phishing Attack (source)
- Lazarus hackers breach six companies in watering hole attacks (source)
- Chinese Hackers Abuse IPv6 SLAAC for AitM Attacks via Spellbinder Lateral Movement Tool (source)
- Chinese hackers behind attacks targeting SAP NetWeaver servers (source)
- Hackers now testing ClickFix attacks against Linux targets (source)