Security News > 2020 > December > Russian APT28 Hackers Using COVID-19 as Bait to Deliver Zebrocy Malware
A Russian threat actor known for its malware campaigns has reappeared in the threat landscape with yet another attack leveraging COVID-19 as phishing lures, once again indicating how adversaries are adept at repurposing the current world events to their advantage.
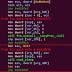
Linking the operation to a sub-group of APT28, cybersecurity firm Intezer said the pandemic-themed phishing emails were employed to deliver the Go version of Zebrocy malware.
Zebrocy is delivered primarily via phishing attacks that contain decoy Microsoft Office documents with macros as well as executable file attachments.
The second file is an executable that masquerades as a Word document that, when opened, runs the Zebrocy malware.
The Golang version of the Zebrocy backdoor also caught the attention of the US Cybersecurity and Infrastructure Security Agency, which released an advisory in late October, cautioning that the malware is "Designed to allow a remote operator to perform various functions on the compromised system."
News URL
Related news
- North Korean Hackers Target Freelance Developers in Job Scam to Deploy Malware (source)
- Chinese hackers use custom malware to spy on US telecom networks (source)
- New Linux Malware ‘Auto-Color’ Grants Hackers Full Remote Access to Compromised Systems (source)
- Space Pirates Targets Russian IT Firms With New LuckyStrike Agent Malware (source)
- YouTube Game Cheats Spread Arcane Stealer Malware to Russian-Speaking Users (source)
- Chinese FamousSparrow hackers deploy upgraded malware in attacks (source)
- Russian Hackers Exploit CVE-2025-26633 via MSC EvilTwin to Deploy SilentPrism and DarkWisp (source)
- North Korean Hackers Deploy BeaverTail Malware via 11 Malicious npm Packages (source)
- Russian hackers attack Western military mission using malicious drive (source)
- Chinese Hackers Target Linux Systems Using SNOWLIGHT Malware and VShell Tool (source)