Security News

Microsoft has addressed a bug causing Windows Search and the Start Menu to become unresponsive and some Windows applications to no longer open. "The Start menu, Windows search, and Universal Windows Platform apps might not work as expected or might have issues opening," Microsoft says on the Windows health dashboard.

Pub The command will print out your SSH key on your Linux machine without prompting you for your key authentication password. How to view your SSH public key on macOS. Viewing your keys on macOS can be done in a similar fashion as on Linux.

Cybersecurity firm Trellix has addressed an incompatibility issue causing Endpoint Security Agent's Exploit Guard module to block some Microsoft Office and third-party apps from opening after...

A previously undocumented Windows-based information stealer called ThirdEye has been discovered in the wild with capabilities to harvest sensitive data from infected hosts. The arrival vector for the malware is presently unknown, although the nature of the lure points to it being used in a phishing campaign.

Microsoft has addressed a known issue causing File Explorer on Windows 11 and Windows Server systems after viewing a file's effective access permissions. The known issue impacts systems running the latest Windows releases, including Windows 11 21H2/22H2 and Windows Server 2022.

Microsoft has released the optional KB5027293 Preview cumulative update for Windows 10 22H2 with three new features and 11 additional fixes or changes. Windows 10 users can also manually download and install the KB5027293 preview update from the Microsoft Update Catalog.

Microsoft has released the June 2023 optional cumulative update for Windows 11, version 22H2, which enables the recently announced new Moment 3 fixes, improvements, and new features. While Moment 3 changes have been disabled by default, even though included with the KB5026446 update, users could still enable them by turning on a toggle in the Windows Update settings.

Microsoft is expanding support for passkeys in Windows 11 to make it more secure to log into websites and apps using biometric authentication. To use passkeys on your Windows device for website sign-ins, you have to go to passkey-enabled websites like bestbuy.com, ebay.com, or google.com, create a passkey by accessing from your account settings, and then sign out of your account and then sign back in using your newly created passkey.

A trojanized installer for the popular Super Mario 3: Mario Forever game for Windows has been infecting unsuspecting players with multiple malware infections. Super Mario 3: Mario Forever is a free-to-play remake of the classic Nintendo game developed by Buziol Games and released for the Windows platform in 2003.
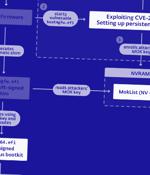
The U.S. National Security Agency on Thursday released guidance to help organizations detect and prevent infections of a Unified Extensible Firmware Interface bootkit called BlackLotus. A UEFI bootkit capable of bypassing Windows Secure Boot protections, samples of the malware have since emerged in the wild.