Security News

The Quad7 botnet is expanding its targeting scope with the addition of new clusters and custom implants that now also target Zyxel VPN appliances and Ruckus wireless routers. [...]

Compare Surfshark and NordVPN to determine which one is better. Explore their features, performance and pricing to make an informed decision.

A new malware campaign is spoofing Palo Alto Networks' GlobalProtect VPN software to deliver a variant of the WikiLoader (aka WailingCrab) loader by means of a search engine optimization (SEO)...

Looking for the best VPN services for SMBs? Here's a comprehensive guide covering the top options for secure remote access and data protection on a budget.
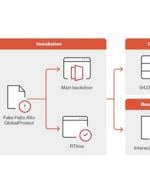
Cybersecurity researchers have disclosed a new campaign that potentially targets users in the Middle East through malware that disguises itself as Palo Alto Networks GlobalProtect virtual private...

While Proton VPN’s strong focus on privacy is enticing, NordVPN’s fast-performing and all-around VPN service is the better overall package between the two.

While CyberGhost VPN’s optimized servers bring a lot of value, NordVPN’s more consistent speed performance and extensive feature inclusions give it the slight edge.

The threat actors behind a recently observed Qilin ransomware attack have stolen credentials stored in Google Chrome browsers on a small set of compromised endpoints. The use of credential...

While CyberGhost VPN presents an impressive amount of servers, ExpressVPN’s consistent VPN speeds and strong third-party audits give it the edge.

ExpressVPN’s overall polish, fast performance and wider server network give it a slight edge over PIA VPN’s feature-rich and affordable package.