Security News

The issue began yesterday, and although it does not appear to impact everyone, it is far from isolated, with affected users reporting that it affects all YouTube videos. The reports come from users of ad blockers on both Chrome and Firefox, like Adblock Plus, as well as web browsers that have integrated ad-blocking systems, such as OperaGX. A first reported by 9to5Google, many users are accusing YouTube of intentionally causing this problem, as Google has begun cracking down on the use of ad blockers on YouTube over the past year.

YouTube is no longer showing recommended videos to users logged out of a Google account or using Incognito mode, making people concerned they are being bullied into always being signed into the service. This change, which is now rolling out, shows a simple YouTube homepage without any videos or tips on what to watch.
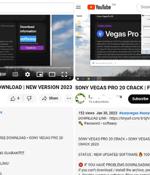
Threat actors are resorting to YouTube videos featuring content related to cracked software in order to entice users into downloading an information stealer malware called Lumma. “These YouTube...

TikTok is flooded with videos promoting fake nude celebrity photo leaks used to push referral rewards for the Temu online megastore. Lately, Temu referral codes on TikTok have taken a darker turn, with scammers creating videos that imply sensitive photos and videos of celebrities have been leaked.

Google has backtracked on its plan to delete inactive YouTube videos-at least for now. Of course, it could change its mind anytime it wants.

YouTube is running an experiment asking some users to disable their ad blockers or pay for a premium subscription, or they will not be allowed to watch videos. Upon receiving this notification, users will have two options: either disable their ad blocker to allow YouTube ads or consider subscribing to YouTube Premium to get rid of all advertisements.
Cybersecurity researchers have detailed the inner workings of a highly evasive loader named "In2al5d p3in4er" that's used to deliver the Aurora information stealer malware. "The in2al5d p3in4er loader is compiled with Embarcadero RAD Studio and targets endpoint workstations using advanced anti-VM technique," cybersecurity firm Morphisec said in a report shared with The Hacker News.

Grand Theft Auto 6 gameplay videos and source code have been leaked after a hacker allegedly breached Rockstar Game's Slack server and Confluence wiki.Some of the videos contain voiced conversations between the protagonist and other NPCs. The hacker claims to have stolen "GTA 5 and 6 source code and assets, GTA 6 testing build," but is trying to extort Rockstar Games to prevent further data from being released.

A new malware bundle uses victims' YouTube channels to upload malicious video tutorials advertising fake cheats and cracks for popular video games to spread the malicious package further. The self-spreading malware bundle has been promoted in YouTube videos targeting fans playing FIFA, Final Fantasy, Forza Horizon, Lego Star Wars, and Spider-Man.

Amazon has revealed that it gives police videos from its Ring doorbells without a warrant and without user consent. The Amazon company responded to an inquiry from US Senator Ed Markey, confirming that there have been 11 cases in 2022 where Ring complied with police "Emergency" requests.