Security News

Yet another cash grab from Kim's cronies and an intel update from Microsoft North Korea has changed tack: its latest campaign targets the NPM registry and owners of Exodus and Atomic...

Organizations’ increasing reliance on third-party software and services has created an environment with more vulnerabilities and harder-to-detect risks. Attackers know they can increase efficiency...

Imagine you're considering a new car for your family. Before making a purchase, you evaluate its safety ratings, fuel efficiency, and reliability. You might even take it for a test drive to ensure...

When cloud customers don't clean up after themselves, part 97 Abandoned AWS S3 buckets could be reused to hijack the global software supply chain in an attack that would make Russia's "SolarWinds...

Threat actor exploited phishing and OAuth abuse to inject malicious code Cybersecurity outfit Sekoia is warning Chrome users of a supply chain attack targeting browser extension developers that...

South Korean VPN provider IPany was breached in a supply chain attack by the "PlushDaemon" China-aligned hacking group, who compromised the company's VPN installer to deploy the custom...
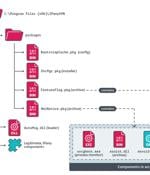
A previously undocumented China-aligned advanced persistent threat (APT) group named PlushDaemon has been linked to a supply chain attack targeting a South Korean virtual private network (VPN)...

ESET researchers have uncovered a supply chain attack targeting a South Korean VPN provider, carried out by PlushDaemon, a newly identified China-aligned APT group. In this cyberespionage...

'The greatest concern is with spear phishing and social engineering' Interview Now that criminals have realized there's no need to train their own LLMs for any nefarious purposes - it's much...

The developers of Rspack have revealed that two of their npm packages, @rspack/core and @rspack/cli, were compromised in a software supply chain attack that allowed a malicious actor to publish...