Security News
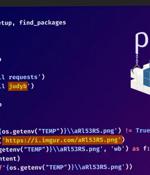
An ongoing supply chain attack has been leveraging malicious Python packages to distribute malware called W4SP Stealer, with over hundreds of victims ensnared to date. "The threat actor is still active and is releasing more malicious packages," Checkmarx researcher Jossef Harush said in a technical write-up, calling the adversary WASP. "The attack seems related to cybercrime as the attacker claims that these tools are undetectable to increase sales."

Emotet, one of the most evasive and destructive malware delivery systems, caused substantial damage during its initial reign. After a coordinated takedown by authorities in early 2021, Emotet has reemerged as a global threat that will persist for organizations.

As cyber attackers increasingly look to capitalize on accelerating digitalization that has seen many enterprises significantly increase their reliance on cloud-based solutions and services as well as third-party service providers, software supply chain risk has become a major concern of organizations. In this Help Net Security video, Andy Zollo, Regional VP of EMEA at Imperva, talks about how organizations can assess and mitigate cyber risks within their supply chain.

Prevention is often seen as the responsibility of the software developer, as they are required to securely develop and deliver code, verify third party components, and harden the build environment. The supplier also holds a critical responsibility in ensuring the security and integrity of our software.

Threat actors are using the compromised infrastructure of an undisclosed media company to deploy the SocGholish JavaScript malware framework on the websites of hundreds of newspapers across the U.S. "The media company in question is a firm that provides both video content and advertising to major news outlets. [It] serves many different companies in different markets across the United States," Sherrod DeGrippo, VP of threat research and detection at Proofpoint, told BleepingComputer. The threat actor behind this supply-chain attack has injected malicious code into a benign JavaScript file that gets loaded by the news outlets' websites.

Threat actors are using the compromised infrastructure of an undisclosed media company to deploy the SocGholish JavaScript malware framework on the websites of hundreds of newspapers across the U.S. The threat actor behind this supply-chain attack has injected malicious code into a benign JavaScript file that gets loaded by the news outlets' websites. "Proofpoint Threat Research has observed intermittent injections on a media company that serves many major news outlets. This media company serves content via Javascript to its partners," Proofpoint's Threat Insight team revealed today in a Twitter thread. "By modifying the codebase of this otherwise benign JS, it is now used to deploy SocGholish."

Recent cyberthreats have highlighted security gaps in the software supply chain, and enterprises must take a closer look at their third-party due diligence processes to ensure trust and security. In a recent survey conducted by the Neustar International Security Council, 76% of security and information technology professionals worldwide cited software supply chain risk as a top security priority, and fully 77% attributed the increased rigor of due diligence processes they have in place for external managed service providers to the Log4j vulnerability and other prominent attacks against software and service providers.

NSA, CISA, and the Office of the Director of National Intelligence have shared a new set of suggested practices that software suppliers can follow to secure the supply chain. "Prevention is often seen as the responsibility of the software developer, as they are required to securely develop and deliver code, verify third party components, and harden the build environment. But the supplier also holds a critical responsibility in ensuring the security and integrity of our software," the NSA said on Monday.

Each of these "Bricks" is itself the product of a long supply chain, making the software supply chain a concept that encompasses every facet of IT: from hardware, to source code written by developers, to third-party tools and platforms, but also data storage and all the infrastructures put in place to develop, test and distribute the software. Software supply chains have many grey areas that are not addressed by traditional security methods.

In brief Google has released a new open source software tool to help businesses better understand the risks to their software supply chains by aggregating security metadata into a queryable, standardized database. The Graph for Understanding Artifact Composition, or "GUAC" - pronounced like the avocado dip - "Aggregates and synthesizes software security metadata at scale and makes it meaningful and actionable," Google said in a blog post.