Security News

Law enforcement authorities have announced that they tracked down the customers of the SmokeLoader malware and detained at least five individuals. "In a coordinated series of actions, customers of...

In follow-up activity for Operation Endgame, law enforcement tracked down Smokeloader botnet's customers and detained at least five individuals. [...]
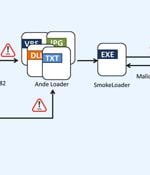
Taiwanese entities in manufacturing, healthcare, and information technology sectors have become the target of a new campaign distributing the SmokeLoader malware. "SmokeLoader is well-known for...

Financially motivated hackers have been leveraging SmokeLoader malware in a series of phishing campaigns predominantly targeting Ukrainian government and administration organizations. The Ukrainian SSSCIP State Cyber Protection Center, together with the Palo Alto Networks Unit 42 research team, have been tracking a massive phishing campaign linked to the distribution of the SmokeLoader malware.

The threat actors behind the 8Base ransomware are leveraging a variant of the Phobos ransomware to conduct their financially motivated attacks. The findings come from Cisco Talos, which has...
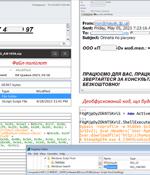
An ongoing phishing campaign with invoice-themed lures is being used to distribute the SmokeLoader malware in the form of a polyglot file, according to the Computer Emergency Response Team of Ukraine. In a related advisory, Ukraine's cybersecurity authority also revealed details of destructive attacks orchestrated by a group known as UAC-0165 against public sector organizations.

Cryptocurrency users are being targeted with a new clipper malware strain dubbed Laplas by means of another malware known as SmokeLoader. Observed in the wild since circa 2013, SmokeLoader functions as a generic loader capable of distributing additional payloads onto compromised systems, such as information-stealing malware and other implants.
An information-stealing malware called Amadey is being distributed by means of another backdoor called SmokeLoader. The attacks hinge on tricking users into downloading SmokeLoader that masquerades as software cracks, paving the way for the deployment of Amadey, researchers from the AhnLab Security Emergency Response Center said in a report published last week.

A new version of the Amadey Bot malware is distributed through the SmokeLoader malware, using software cracks and keygen sites as lures. Amadey Bot is a malware strain discovered four years ago, capable of performing system reconnaissance, stealing information, and loading additional payloads.

Check Point has published its latest Global Threat Index for December 2018. The index reveals that SmokeLoader, a second-stage downloader known to researchers since 2011, rose 11 places in...