Security News

A coordinated international law enforcement exercise has taken down the online infrastructure associated with a cross-platform remote access trojan known as NetWire. "NetWire is a licensed commodity RAT offered in underground forums to non-technical users to carry out their own criminal activities," Europol's European Cybercrime Center said in a tweet.

Worldwiredlabs.com, a domain utilized by cybercriminals to distribute the NetWire remote access trojan allowed perpetrators to assume control of infected computers and extract a diverse range of sensitive information from their unsuspecting victims. Law enforcement in Switzerland seized the computer server hosting the NetWire RAT infrastructure.

International law enforcement agencies have claimed another victory over cyber criminals, after seizing the website, and taking down the infrastructure operated by crims linked to the NetWire remote access trojan. On the same day, a US judge approved a seizure warrant that allowed federal authorities in Los Angeles to seize the internet domain, and Swiss law enforcement seized the server hosting the NetWire RAT infrastructure.

An international law enforcement operation involving the FBI and police agencies worldwide led to the arrest of the suspected administrator of the NetWire remote access trojan and the seizure of the service's web domain and hosting server. Since at least 2014, NetWire has been a tool of choice in various malicious activities, including phishing attacks, BEC campaigns, and to breach corporate networks.

Cybercriminals are disguising the PlugX remote access trojan as a legitimate open-source Windows debugging tool to evade detection and compromise systems. In a recent case detailed by Trend Micro, miscreants used a PlugX variant to hijack the popular x64dbg debugging tool to go undetected.

Cryptocurrency companies are being targeted as part of a new campaign that delivers a remote access trojan called Parallax RAT. The malware "Uses injection techniques to hide within legitimate processes, making it difficult to detect," Uptycs said in a new report. Parallax RAT grants attackers remote access to victim machines.

Orcus RAT is a type of malicious software program that enables remote access and control of computers and networks. There are several lifehacks that you should pay attention to while performing the analysis of Orcus RAT. Today we investigate the.
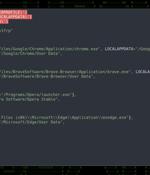
Cybersecurity researchers have unearthed a new Python-based attack campaign that leverages a Python-based remote access trojan to gain control over compromised systems since at least August 2022. LNK files retrieves two text files from a remote server that are subsequently renamed to.

A new Python-based malware has been spotted in the wild featuring remote access trojan capabilities to give its operators control over the breached systems. The PY#RATION malware is distributed via a phishing campaign that uses password-protected ZIP file attachments containing two shortcut.

The threat actor behind the BlackRock and ERMAC Android banking trojans has unleashed yet another malware for rent called Hook that introduces new capabilities to access files stored in the devices and create a remote interactive session. ThreatFabric, in a report shared with The Hacker News, characterized Hook as a novel ERMAC fork that's advertised for sale for $7,000 per month while featuring "All the capabilities of its predecessor."