Security News

Security researchers have disclosed multiple architectural vulnerabilities in Siemens SIMATIC and SIPLUS S7-1500 programmable logic controllers that could be exploited by a malicious actor to stealthily install firmware on affected devices and take control of them. Put differently, the weaknesses are the result of a lack of asymmetric signature verifications for firmware at bootup, effectively permitting the attacker to load tainted bootloader and firmware while undermining integrity protections.

The U.S. Cybersecurity and Infrastructure Security Agency this week released an Industrial Control Systems advisory warning of multiple vulnerabilities in Mitsubishi Electric GX Works3 engineering software. "Successful exploitation of these vulnerabilities could allow unauthorized users to gain access to the MELSEC iQ-R/F/L series CPU modules and the MELSEC iQ-R series OPC UA server module or to view and execute programs," the agency said.

The U.S. Cybersecurity and Infrastructure Security Agency this week released an Industrial Control Systems advisory warning of multiple vulnerabilities in Mitsubishi Electric GX Works3 engineering software. "Successful exploitation of these vulnerabilities could allow unauthorized users to gain access to the MELSEC iQ-R/F/L series CPU modules and the MELSEC iQ-R series OPC UA server module or to view and execute programs," the agency said.

A vulnerability in Siemens Simatic programmable logic controller can be exploited to retrieve the hard-coded, global private cryptographic keys and seize control of the devices. "An attacker can use these keys to perform multiple advanced attacks against Siemens SIMATIC devices and the related TIA Portal, while bypassing all four of its access level protections," industrial cybersecurity company Claroty said in a new report.
A hacktivist collective called GhostSec has claimed credit for compromising as many as 55 Berghof programmable logic controllers used by Israeli organizations as part of a "Free Palestine" campaign. "The group pivoted from their regular operations and started to target multiple Israeli companies, presumably gaining access to various IoT interfaces and ICS/SCADA systems, which led to possible disruptions," Cyberint noted on July 14.
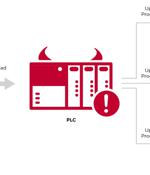
With the Evil PLC attack, the controller acts as a means to an end, permitting the threat actor to breach a workstation, access to all the other PLCs on the network, and even tamper with the controller logic. Put differently, the idea is to "Use the PLC as a pivot point to attack the engineers who program and diagnose it and gain deeper access to the OT network," the researchers said.