Security News

Signal is now testing public usernames that allow users to conceal the phone numbers linked to their accounts while communicating with others. "Think of The Staging Environment as a parallel Signal universe: you'll need to install and run a new build, and register for a new account with a phone number," O'Leary said.

"Specifically, we found mobile device management issues that put ICE mobile devices - and potentially other mobile devices demonstrating similar issues - and sensitive data at greater risk of potential espionage, leaks, and attacks from viruses," wrote Inspector General Joseph Cuffari in a redacted report [PDF]. While we don't know which of these naughty-list apps auditors found on ICE employees phones, it's probably safe to assume one of the offenders was TikTok - banned from US federal government staff and contractors' devices because of espionage concerns, due to the influence the Chinese government can exert over Beijing-based parent ByteDance.

Czech cybersecurity company Avast confirmed that its antivirus SDK has been flagging a Google Android app as malware on Huawei, Vivo, and Honor smartphones since Saturday. Others saw a different alert, telling them that the Google app was a trojan that could provide remote access to their device and allow attackers to install malware and steal the users' data.

Huawei, Honor, and Vivo smartphones and tablets are displaying strange 'Security threat' alerts urging the deletion of the Google app, warning that it is detected as the 'TrojanSMS-PA' malware. BleepingComputer contacted Google to determine if a recent app update might have caused the sudden uptick in malware warnings, but a spokesperson said Google Play Protect is not triggering the alert.

Meta announced today that it's rolling out support for multiple WhatsApp accounts on the same device, allowing users to switch between them without needing to log out. "Today, we're introducing the ability to have two WhatsApp accounts logged in at the same time," the company said on Thursday.
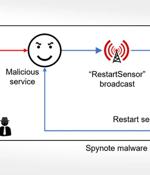
The Android banking trojan known as SpyNote has been dissected to reveal its diverse information-gathering features. Typically spread via SMS phishing campaigns, attack chains involving the...

A key monetization mechanism of a sophisticated series of cybercriminal operations involving backdoored off-brand mobile and CTV Android devices has been disrupted, Human Security has announced. Badbox-infected devices are able to steal personally identifiable information, establish residential proxy exit peers, steal one-time passwords, create fake messaging and email accounts, and other unique fraud schemes.

The U.S. Federal Emergency Management Agency and the Federal Communications Commission will run an emergency alert test today to check Emergency Alert System and Wireless Emergency Alerts capabilities nationwide. On consumers' phones, WEA alert messages will read: "This is a test of the National Wireless Emergency Alert System. No action is needed."

That's because "Fake airplane" mode doesn't itelf snoop on or try to steal private data belonging to other apps, but works simply by showing you what you hope to see, namely visual clues that imply that your device is offline even when it isn't. You can imagine that determined scammers, cryptoconfidence tricksters and spyware peddlers might be keen to find a way to hide "Fake airplane" treachery in otherwise unexceptionable looking apps in order to make it through the App Store verification process.
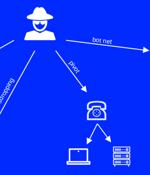
Multiple security vulnerabilities have been disclosed in AudioCodes desk phones and Zoom's Zero Touch Provisioning that could be potentially exploited by a malicious attacker to conduct remote attacks. "An external attacker who leverages the vulnerabilities discovered in AudioCodes Ltd.'s desk phones and Zoom's Zero Touch Provisioning feature can gain full remote control of the devices," SySS security researcher Moritz Abrell said in an analysis published Friday.