Security News

The North Korean-backed Lazarus hacking group used new malware with backdoor capabilities dubbed Vyveva n targeted attacks against a South African freight logistics company. Vyveva was first used in a June 2020 attack as ESET researchers discovered, but further evidence shows Lazarus has been deploying it in previous attacks going back to at least December 2018.

The same North Korean threat actors that targeted security researchers in January appear to be readying a new campaign using a fake company that aim to lure security professionals into another cyber-espionage trap. While researchers have seen no evidence yet of nefarious activity from attackers that leverage these web assets, it appears that attackers are gearing up to target security researchers again by the nature of the activity, according to Google TAG. Like previous websites that Google TAG has observed Zinc establish, the SecuriElite website has a link to the group's PGP public key at the bottom of the page, researchers noted.

A North Korean government-backed APT group has been caught using a fake pen-testing company and a range of sock puppet social media accounts in an escalation of a hacking campaign targeting security research professionals. The notorious hacking group, first exposed by Google earlier this year, returned on March 17th with a website for a fake penetration testing company.

Google's Threat Analysis Group says that North Korean government-sponsored hackers are once again targeting security researchers using fake Twitter and LinkedIn social media accounts. The hackers also created a website for a fake company named SecuriElite and supposedly offering offensive security services as the Google security team focused on hunting down state-backed hackers discovered on March 17.
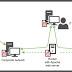
A prolific North Korean state-sponsored hacking group has been tied to a new ongoing espionage campaign aimed at exfiltrating sensitive information from organizations in the defense industry. The next-stage malware functions by embedding its malicious capabilities inside a Windows backdoor that offers features for initial reconnaissance and deploying malware for lateral movement and data exfiltration.

During an attack on the defense industry, the North Korea-linked threat group known as Lazarus was able to exfiltrate data from a restricted network segment by taking control of a router and setting it up as a proxy server. They were even able to steal data from a network segment that was cut off from the internet, by compromising a router used to connect to it.

Kaspersky security researchers have found evidence that the North Korean hacking collective known as Lazarus has added another target to its list of victims: The defense industry, and companies in more than a dozen countries have already been affected. As previously reported by TechRepublic, Lazarus started off 2021 by targeting security researchers with offers of collaborating on malware research, only to infect victims with malware that could cause the theft of sensitive security-related data.

A North Korean-backed hacking group has targeted the defense industry with custom backdoor malware dubbed ThreatNeedle since early 2020 with the end goal of collecting highly sensitive information. ThreatNeedle helped the Lazarus hackers to move laterally throughout the defense orgs' networks and harvest sensitive info that got exfiltrated to attacker-controlled servers using a custom tunneling tool via SSH tunnels to remote compromised South Korean servers.

The US Department of Justice has just unsealed a lengthy list of cybercrime charges against three North Koreans. The DOJ explicitly named the three accused men as Jon Chang Hyok, Kim Il, and Park Jin Hyok, alleging them to be part of a North Korean hacking group that you may have heard referred to over the years as APT38 or the Lazarus Group.

The FBI, CISA, and US Department of Treasury shared detailed info on malicious and fake crypto-trading applications used by North Korean-backed state hackers to steal cryptocurrency from individuals and companies worldwide in a joint advisory published on Wednesday. "It is likely that these actors view modified cryptocurrency trading applications as a means to circumvent international sanctions on North Korea-the applications enable them to gain entry into companies that conduct cryptocurrency transactions and steal cryptocurrency from victim accounts."