Security News

OpenAI has shut down five accounts it asserts were used by government agents to generate phishing emails and malicious software scripts as well as research ways to evade malware detection. "We disrupted five state-affiliated malicious actors: two China-affiliated threat actors known as Charcoal Typhoon and Salmon Typhoon; the Iran-affiliated threat actor known as Crimson Sandstorm; the North Korea-affiliated actor known as Emerald Sleet; and the Russia-affiliated actor known as Forest Blizzard," the OpenAI team wrote.

The North Korea-linked nation-state actor known as Kimsuky is suspected of using a previously undocumented Golang-based information stealer called Troll Stealer. The malware steals "SSH,...

Threat actors affiliated with the Democratic People's Republic of Korea (also known as North Korea) have plundered at least $600 million in cryptocurrency in 2023. The DPRK "was responsible for...

Interpol on Tuesday revealed the results of what it's dubbed Operation HAECHI IV - a six-month effort that saw 34 nations cooperate, with funding from South Korea. The majority - about three quarters - of the crime investigated by the op was business email compromise, e-commerce fraud, and investment fraud.

Updated The offensive cyber unit linked to Russia's Foreign Intelligence Service is exploiting the critical vulnerability affecting the JetBrains TeamCity CI/CD server at scale, and has been since September, authorities warn. The exploit in TeamCity could give attackers enough access to manipulate a software's source code, sign certificates, and compile and deploy processes, the advisory says.

The North Korean threat actor known as Kimsuky has been observed targeting research institutes in South Korea as part of a spear-phishing campaign with the ultimate goal of distributing backdoors...

North Korean-backed state hackers have stolen an estimated $3 billion in a long string of hacks targeting the cryptocurrency industry over the last six years since January 2017. "Since 2017, North Korea has significantly increased its focus on the cryptocurrency industry, stealing an estimated $3 billion worth of cryptocurrency," Recorded Future analysts said.
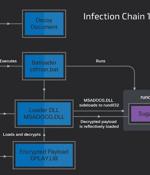
A suspected Chinese-speaking threat actor has been attributed to a malicious campaign that targets the Uzbekistan Ministry of Foreign Affairs and South Korean users with a remote access trojan...

The Treasury Department's Office of Foreign Assets Control has sanctioned the North Korean-backed Kimsuky hacking group for stealing intelligence in support of the country's strategic goals. OFAC has also sanctioned eight North Korean agents for facilitating sanctions evasion and supporting their country's weapons of mass destruction programs.

Threat actors from the Democratic People's Republic of Korea (DPRK) are increasingly targeting the cryptocurrency sector as a major revenue generation mechanism since at least 2017 to get around...