Security News

The annual barometer of industry perceptions and intentions around IoT security surveyed 1,038 technology decision makers across Europe, USA, and APAC, and signals a positive turning point for security with organizations placing it at the center of IoT strategy and organizational culture. Despite almost universal acceptance that IoT security commands a premium, nearly a third of those asked identified cost as inhibiting them from implementing stronger security, while perceived expense and a lack of ROI were the biggest barriers to conducting external lab testing.

As NIST research shows security flaws continue to pile up, this haphazard approach will surely catch up to teams who rely exclusively on responsive rather than proactive security strategies. In the past, IoT security considerations were far too often overlooked in the name of increasing speed to market and reducing costs - security was at most a box to be checked at the end of development.

The IoT in manufacturing market 2021 value stood at an estimated $62.1 billion, and it will increase to $200.3 billion by 2030, at a 13.9% CAGR between 2021 and 2030, according to P&S Intelligence. To further enhance the IoT solutions in use, industrialists are deploying artificial intelligence to analyze the data generated by IoT sensors in real time and make sound decisions.

The current device discovery solutions have been mainly focused on identifying and monitoring servers, workstation PCs, laptops and infrastructure devices such as network firewalls, switches and routers, because the most valuable information assets of organizations are being stored, processed and transferred over those devices, hence making them the prime target of security breaches and intrusions. Accurate identification of connected device manufacturer, model name, device type, device end of life status, firmware version, and firmware release date.

The global IoT in smart cities market size to grow from $130.6 billion in 2021 to $132.2 billion by 2026, at a Compound Annual Growth Rate of 19.0 % during the forecast period, according to ResearchAndMarkets. The service segment in the IoT in smart cities market to have a higher CAGR. The services segment in the IoT in smart cities market is expected to grow, as major players are focused on offering services.

35% of the growth will originate from North America for the IoT data management market. The IoT data management market is expected to grow by $94.79 billion from 2021 to 2026.

Electromagnetic emanations can be recorded and used to detect and identify malware running on IoT devices, a group of researchers working at IRISA have proven. This novel malware detection approach also offers additional advantages: as no specific software has to be installed on the monitored device, it can hardly be detected by the malware and evaded by the malware authors.
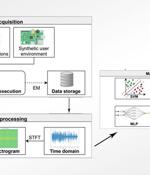
Cybersecurity researchers have proposed a novel approach that leverages electromagnetic field emanations from the Internet of Things devices as a side-channel to glean precise knowledge about the different kinds of malware targeting the embedded systems, even in scenarios where obfuscation techniques have been applied to hinder analysis. With the rapid adoption of IoT appliances presenting an attractive attack surface for threat actors, in part due to them being equipped with higher processing power and capable of running fully functional operating systems, the latest research aims to improve malware analysis to mitigate potential security risks.

LTE IoT market is expected to register a healthy CAGR of over 28% during the forecast period, accordig to ResearchAndMarkets. The growth of connected devices and the need for unique and defined network qualities are fueling the growth of the LTE IoT market.

Even when the mobile phone age arrived, the Chatter Phone retained its dial, its cheese-dish phone styling, and its sideways receiver. We don't how how or if you can dial the plus symbol for overseas calls, but many countries let you use a special digit sequence instead. So, the Chatter Telephone doesn't take a SIM card itself; instead, it pairs with a regular mobile phone and acts, if you like, as a sort of extension - a happy, smiley, cheerful, brightly coloured, child-like extension phone with an actual rotary dial.