Security News
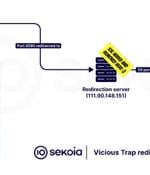
Cybersecurity researchers have disclosed that a threat actor codenamed ViciousTrap has compromised nearly 5,300 unique network edge devices across 84 countries and turned them into a honeypot-like...

Beelzebub is an open-source honeypot framework engineered to create a secure environment for detecting and analyzing cyber threats. It features a low-code design for seamless deployment and...

Trapster Community is an open-source, lightweight, low-interaction honeypot designed for deployment within internal networks. It enhances network security by creating a deceptive layer that...

Microsoft is using deceptive tactics against phishing actors by spawning realistic-looking honeypot tenants with access to Azure and lure cybercriminals in to collect intelligence about them. [...]

Respotter is an open-source honeypot designed to detect attackers when they launch Responder within your environment. This application identifies active instances of Responder by exploiting its...

The online criminal bazaar BreachForums has been resurrected merely two weeks after a U.S.-led coordinated law enforcement action dismantled and seized control of its infrastructure. Cybersecurity...

Attackers typically find exposed "Secrets" - pieces of sensitive information that allow access to an enterprise cloud environment - in as little as two minutes and, in many cases, begin exploiting them almost instantly, highlighting the urgent need for comprehensive cloud security, according to Orca Security. Orca's research was conducted between January and May 2023, beginning with the creation of "Honeypots" on nine different cloud environments that simulated misconfigured resources in the cloud to entice attackers.

Hackers swarm to RDP. An experiment using high-interaction honeypots with an RDP connection accessible from the public web shows how relentless attackers are and that they operate within a daily schedule very much like working office hours. The attack count for the entire year reached 13 million login attempts.

Game developer Valve has announced that it permanently banned more than 40,000 accounts for using cheating software to gain an unfair advantage over other players in the Dota 2 game. The cheat gave players access to internal client app information that is not visible during normal gameplay, thus obtaining a competitive advantage.

CryPLH is a low-interactive and virtual Smart-Grid ICS honeypot simulating Siemens Simatic 300 PLC devices. With the development of cybersecurity technology, deception has been applied in various circumstances like the web, databases, mobile apps, and IoT. Deception technology has been embodied in some ICS honeypot applications in the OT field.