Security News

The attack works by using the device's speaker to issue voice commands. As long as the speech contains the device wake word followed by a permissible command, the Echo will carry it out, researchers from Royal Holloway University in London and Italy's University of Catania found.

Pangu Lab in China just published a report of a hacking operation by the Equation Group (aka the NSA). It noticed the hack in 2013, and was able to map it with Equation Group tools published by...

Russia will consider any cyberattacks targeting Russian satellite infrastructure an act of war, as the country's space agency director said in a TV interview. Dmitry Rogozin, the current head of the Russian Roscosmos State Space Corporation, added that such attempts would also be considered crimes and investigated by Russia's law enforcement agencies.

The All-In-One 2022 Super-Sized Ethical Hacking Bundle helps you gain both, with 18 courses covering all aspects of cybersecurity. The purpose of ethical hacking is to find weaknesses in the system that a malicious hacker may exploit.

Users of Horde Webmail are being urged to disable a feature to contain a nine-year-old unpatched security vulnerability in the software that could be abused to gain complete access to email accounts simply by previewing an attachment. "This gives the attacker access to all sensitive and perhaps secret information a victim has stored in their email account and could allow them to gain further access to the internal services of an organization," SonarSource vulnerability researcher, Simon Scannell, said in a report.
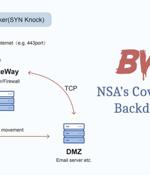
Researchers from China's Pangu Lab have disclosed details of a "Top-tier" backdoor put to use by the Equation Group, an advanced persistent threat with alleged ties to the cyber-warfare intelligence-gathering unit of the U.S. National Security Agency. Equation Group's malware toolset became public knowledge in 2016 when a group calling itself the Shadow Brokers leaked the entire tranche of exploits used by the elite hacking team, with Kaspersky uncovering code-level similarities between the stolen files and that of samples identified as used by the threat actor.

Entities in the aviation, aerospace, transportation, manufacturing, and defense industries have been targeted by a persistent threat group since at least 2017 as part of a string of spear-phishing campaigns mounted to deliver a variety of remote access trojans on compromised systems. The use of commodity malware such as AsyncRAT and NetWire, among others, has led enterprise security firm Proofpoint to a "Cybercriminal threat actor" codenamed TA2541 that employs "Broad targeting with high volume messages." The ultimate objective of the intrusions is unknown as yet.

Researchers at SentinelLabs in a report today detail the tactics of ModifiedElephant explaining how recently published evidence helped them attribute previously "Orphan" attacks. ModifiedElephant has relied on spear-phishing emails with malicious attachments for over a decade now, but their techniques have evolved throughout that time.
Russia arrested six people today, allegedly part of a hacking group involved in the theft and selling of stolen credit cards. Russian media reports that the arrests come at the request of investigators from the Ministry of Internal Affairs of the Russian Federation.
Russia arrested six people today, allegedly part of a hacking group that was involved in the theft and selling of stolen credit cards. Russian media reports that the arrests come at the request of investigators from the Ministry of Internal Affairs of the Russian Federation.