Security News

12.8 million new secrets occurrences were leaked publicly on GitHub in 2023, +28% compared to 2022, according to GitGuardian. Remarkably, the incidence of publicly exposed secrets has quadrupled since the company started reporting in 2021.
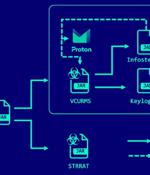
A new phishing campaign has been observed delivering remote access trojans (RAT) such as VCURMS and STRRAT by means of a malicious Java-based downloader. “The attackers stored malware on public...

GitHub users accidentally exposed 12.8 million authentication and sensitive secrets in over 3 million public repositories during 2023, with the vast majority remaining valid after five days. In terms of which sectors leaked the most secrets, IT tops the list with the lion's share of 65.9%, followed by education with a notable 20.1%, and all others combined accounting for 14%. GitGuardian's generic detectors, which caught about 45% of all secrets the firm detected in 2023, are analyzed as follows.

GitHub push protection - a security feature aimed at preventing secrets such as API keys or tokens getting accidentally leaked online - is being switched on by default for all public repositories.Since the beginning of this year, GitHub has detected over 1 million leaked secrets on public repositories, the company also shared.
GitHub on Thursday announced that it’s enabling secret scanning push protection by default for all pushes to public repositories. “This means that when a supported secret is detected in any push...

A malware distribution campaign that began last May with a handful of malicious software packages uploaded to the Python Package Index has spread to GitHub and expanded to reach at least 100,000 compromised repositories. According to security firm Apiiro, the campaign to poison code involves cloning legitimate repos, infecting them with malware loaders, uploading the altered files to GitHub under the same name, then forking the poisoned repo thousands of times and promoting the compromised code in forums and on social media channels.

GitHub has enabled push protection by default for all public repositories to prevent accidental exposure of secrets such as access tokens and API keys when pushing new code. Push protection proactively prevents leaks by scanning for secrets before 'git push' operations are accepted and blocking the commits when a secret is detected.

An "intricately designed" remote access trojan (RAT) called Xeno RAT has been made available on GitHub, making it available to other actors at no extra cost. Written in C# and compatible with...

There is good news, however: high-severity security flaws in applications have decreased by half since 2016, indicating progress in software security practices and that speed of remediation has a material impact on critical security debt. The report reveals development teams that fix flaws the fastest reduce critical security debt by 75%-from 22.4% of applications to just over 5%. Moreover, these fast-acting teams are four times less likely to let critical security debt materialize in their applications in the first place.

A mishandled GitHub token gave unrestricted access to Mercedes-Benz's internal GitHub Enterprise Service, exposing source code to the public. On September 29, 2023, researchers at RedHunt Labs discovered a GitHub token in a public repository belonging to a Mercedez employee that gave access to the company's internal GitHub Enterprise Server.