Security News

Amongst those frameworks, Sliver appeared in 2019 as an open-source framework available on Github and advertised to security professionals. Sliver supports several different network protocols to communicate between the implant and its C2 server: DNS, HTTP/TLS, MTLS, and TCP might be used.

Nation-state threat actors are increasingly adopting and integrating the Sliver command-and-control framework in their intrusion campaigns as a replacement for Cobalt Strike. Sliver, first made public in late 2019 by cybersecurity company BishopFox, is a Go-based open source C2 platform that supports user-developed extensions, custom implant generation, and other commandeering options.

Building your organization's security framework. 3 pro tips for building your lean security framework.

Building your organization's security framework. Why build your security framework from scratch, when you could steal a page from other pros in the space? Get quick tips from their free guide for bootstrapped IT security teams below.

Researchers have disclosed a new offensive framework called Manjusaka that they call a "Chinese sibling of Sliver and Cobalt Strike." "A fully functional version of the command-and-control, written in GoLang with a User Interface in Simplified Chinese, is freely available and can generate new implants with custom configurations with ease, increasing the likelihood of wider adoption of this framework by malicious actors," Cisco Talos said in a new report.

Researchers have observed a new post-exploitation attack framework used in the wild, named Manjusaka, which can be deployed as an alternative to the widely abused Cobalt Strike toolset or parallel to it for redundancy. Its RAT implants support command execution, file access, network reconnaissance, and more, so hackers can use it for the same operational goals as Cobalt Strike.

A never-before-seen Linux malware has been dubbed a "Swiss Army Knife" for its modular architecture and its capability to install rootkits. This previously undetected Linux threat, called Lightning Framework by Intezer, is equipped with a plethora of features, making it one of the most intricate frameworks developed for targeting Linux systems.

A new and previously undetected malware dubbed 'Lightning Framework' targets Linux systems and can be used to backdoor infected devices using SSH and deploy multiple types of rootkits. Described as a "Swiss Army Knife" in a report published today by Intezer, Lightning Framework is a modular malware that also comes with support for plugins.
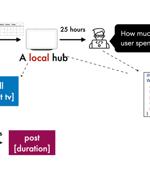
A newly designed privacy-sensitive architecture aims to enable developers to create smart home apps in a manner that addresses data sharing concerns and puts users in control over their personal information. Peekaboo operates on the principle of data minimization, which refers to the practice of limiting data collection to only what is required to fulfill a specific purpose.

It is perhaps better to consider the term zero trust architecture - a framework that requires an organization to take steps depending on the priorities of the business and their current security infrastructure. Whilst it's important for organizations to start making the move to zero trust architecture, it is not as simple as adopting a single vendor's capabilities as a comprehensive solution.