Security News

New Serpent backdoor malware targets French entities with unforeseen method. A new backdoor dubbed Serpent has been found on internet, infecting French entities in the construction and government sectors.

An advanced threat actor has been spotted using distinctive, novel methods to backdoor French entities in the construction, real estate, and government industries. The attack starts with a well-known technique - emails containing a macro-enabled Microsoft Word document masquerading as information relating to the GDPR - and ends up with an attempt to install a backdoor on target systems.
Researchers have exposed a new targeted email campaign aimed at French entities in the construction, real estate, and government sectors that leverages the Chocolatey Windows package manager to deliver a backdoor called Serpent on compromised systems. Enterprise security firm Proofpoint attributed the attacks to a likely advanced threat actor based on the tactics and the victimology patterns observed.

The Daxin malware is taking aim at hardened government networks around the world, according to researchers, with the goal of cyberespionage. "Daxin malware is a highly sophisticated rootkit backdoor with complex, stealthy command-and-control functionality that enabled remote actors to communicate with secured devices not connected directly to the internet," warned CISA, in a Monday alert.

Even as the TrickBot infrastructure closed shop, the operators of the malware are continuing to refine and retool their arsenal to carry out attacks that culminated in the deployment of Conti ransomware. IBM Security X-Force, which discovered the revamped version of the criminal gang's AnchorDNS backdoor, dubbed the new, upgraded variant AnchorMail.
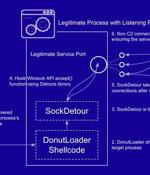
Cybersecurity researchers have taken the wraps off a previously undocumented and stealthy custom malware called SockDetour that targeted U.S.-based defense contractors with the goal of being used as a secondary implant on compromised Windows hosts. "SockDetour is a backdoor that is designed to remain stealthily on compromised Windows servers so that it can serve as a backup backdoor in case the primary one fails," Palo Alto Networks' Unit 41 threat intelligence said in a report published Thursday.

Security researchers have discovered Daxin, a China-linked stealthy backdoor specifically designed for deployment in hardened corporate networks that feature advanced threat detection capabilities. According to a technical report published by Symantec's Threat Hunter team today, Daxin is one of the most advanced backdoors ever seen deployed by Chinese actors.

A new custom malware dubbed SockDetour found on systems belonging to US defense contractors has been used as a backup backdoor to maintain access to compromised networks. SockDetour [.] serves as a backup backdoor in case the primary backdoor is detected and removed by defenders," Unit 42 explained.

A newly discovered custom malware dubbed SockDetour has been found on systems belonging to US defense contractors and used as a backup backdoor to maintain access to compromised networks. SockDetour [.] serves as a backup backdoor in case the primary backdoor is detected and removed by defenders," Unit 42 explained.

Pangu Lab's incident analysis involved three servers, one being the target of an external attack and two other internal machines - an email server and a business server. According to the researchers, the threat actor pivoted established a connection between the external server and the email server via a TCP SYN packet with a 264-byte payload. "At almost the same time, the [email] server connects to the [business] server's SMB service and performs some sensitive operations, including logging in to the [business] server with an administrator account, trying to open terminal services, enumerating directories, and executing Powershell scripts through scheduled tasks" - Pangu Lab.