Security News
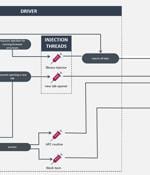
Cybersecurity researchers have shed light on an adware module that purports to block ads and malicious websites, while stealthily offloading a kernel driver component that grants attackers the ability to run arbitrary code with elevated permissions on Windows hosts. The malware, dubbed HotPage, gets its name from the eponymous installer, according to new findings from ESET. The installer "Deploys a driver capable of injecting code into remote processes, and two libraries capable of intercepting and tampering with browsers' network traffic," ESET researcher Romain Dumont said in a technical analysis published today.
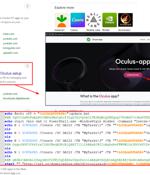
A new campaign is tricking users searching for the Meta Quest (formerly Oculus) application for Windows into downloading a new adware family called AdsExhaust. "The adware is capable of...

Several malicious Google Play Android apps installed over 2 million times push intrusive ads to users while concealing their presence on the infected devices. Dr. Web explains that once victims install these apps on their devices, they hide by replacing their icons with that of Google Chrome or using a transparent icon image to create empty space in the app drawer.

Over 60,000 Android apps disguised as legitimate applications have been quietly installing adware on mobile devices while remaining undetected for the past six months. The malicious apps are not hosted on Google Play but on third-party websites in Google Search that push APKs, Android packages that allow you to manually install mobile apps.

Thousands of adware apps for Android have been found to masquerade as cracks or modded versions of popular apps to redirect users to serve unwanted ads to users as part of a campaign ongoing since October 2022. The Romanian cybersecurity company said it has discovered 60,000 unique apps carrying the adware, with a majority of the detections located in the U.S., South Korea, Brazil, Germany, the U.K., France, Kazakhstan, Romania, and Italy.

A set of 38 Minecraft copycat games on Google Play infected devices with the Android adware 'HiddenAds' to stealthily load ads in the background to generate revenue for its operators. Minecraft is a popular sandbox game with 140 million monthly active players, which numerous game publishers have attempted to recreate.

Security researchers at McAfee have discovered a set of 16 malicious clicker apps that managed to sneak into Google Play, the official app store for Android. Clicker apps are a special category of adware that loads ads in invisible frames or in the background and clicks them to generate revenue for their operators.

Security researchers have discovered 75 applications on Google Play and another ten on Apple's App Store engaged in ad fraud. The Satori team have informed Google and Apple about their findings and the apps have been removed from the official Android and iOS stores.

Google Chrome extension 'Internet Download Manager' installed by more than 200,000 users is adware. Although the extension may install a known and legitimate download manager program, BleepingComputer observed unwanted behavior exhibited by the extension-such as opening links to spammy sites, changing the default browser search engine, and further hounding the user with pop-ups asking them to download more "Patches" and unwanted programs.

Several adware apps promoted aggressively on Facebook as system cleaners and optimizers for Android devices are counting millions of installations on Google Play store. To evade deletion, the apps hide on the victim's device by constantly changing icons and names, masquerading as Settings or the Play Store itself.