Security News > 2025 > January > LDAPNightmare PoC Exploit Crashes LSASS and Reboots Windows Domain Controllers
2025-01-03 08:16
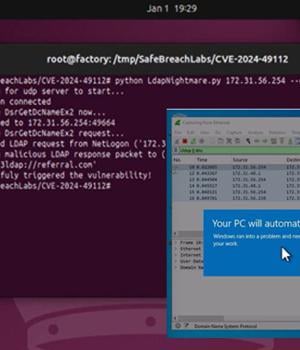
A proof-of-concept (PoC) exploit has been released for a now-patched security flaw impacting Windows Lightweight Directory Access Protocol (LDAP) that could trigger a denial-of-service (DoS) condition. The out-of-bounds reads vulnerability is tracked as CVE-2024-49113 (CVSS score: 7.5). It was addressed by Microsoft as part of Patch Tuesday updates for December 2024, alongside CVE-2024-49112 (
News URL
https://thehackernews.com/2025/01/ldapnightmare-poc-exploit-crashes-lsass.html
Related news
- PipeMagic Trojan Exploits Windows Zero-Day Vulnerability to Deploy Ransomware (source)
- ⚡ Weekly Recap: Windows 0-Day, VPN Exploits, Weaponized AI, Hijacked Antivirus and More (source)
- PoC exploit for critical Erlang/OTP SSH bug is public (CVE-2025-32433) (source)
- PoC exploit for SysAid pre-auth RCE released, upgrade quickly! (source)
Related Vulnerability
| DATE | CVE | VULNERABILITY TITLE | RISK |
|---|---|---|---|
| 2024-12-12 | CVE-2024-49113 | Unspecified vulnerability in Microsoft products Windows Lightweight Directory Access Protocol (LDAP) Denial of Service Vulnerability | 0.0 |
| 2024-12-12 | CVE-2024-49112 | Unspecified vulnerability in Microsoft products Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability | 0.0 |