Security News > 2024 > August > Experts Uncover Severe AWS Flaws Leading to RCE, Data Theft, and Full-Service Takeovers
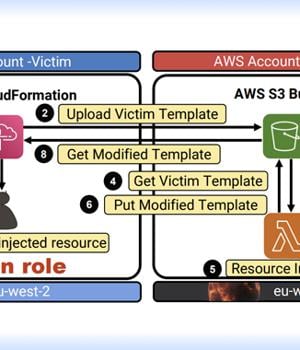
Central to the issue, dubbed Bucket Monopoly, is an attack vector referred to as Shadow Resource, which, in this case, refers to the automatic creation of an AWS S3 bucket when using services like CloudFormation, Glue, EMR, SageMaker, ServiceCatalog, and CodeStar.
An attacker could take advantage of this behavior to set up buckets in unused AWS regions and wait for a legitimate AWS customer to use one of the susceptible services to gain covert access to the contents of the S3 bucket.
Based on the permissions granted to the adversary-controlled S3 bucket, the approach could be used to escalate to trigger a DoS condition, or execute code, manipulate or steal data, and even gain full control over the victim account without the user's knowledge.
To maximize their chances of success, using Bucket Monopoly, attackers can create unclaimed buckets in advance in all available regions and store malicious code in the bucket.
Modifying the CloudFormation template file in the S3 bucket to create a rogue admin user also depends on whether the victim account has permission to manage IAM roles.
"Many open-source projects create S3 buckets automatically as part of their functionality or instruct their users to deploy S3 buckets."
News URL
https://thehackernews.com/2024/08/experts-uncover-severe-aws-flaws.html