Security News > 2024 > July > SocGholish Malware Exploits BOINC Project for Covert Cyberattacks
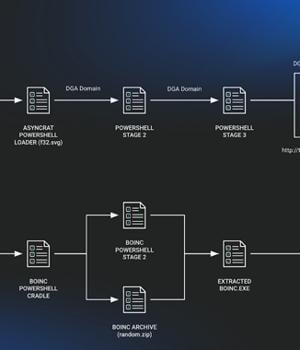
The JavaScript downloader malware known as SocGholish is being used to deliver a remote access trojan called AsyncRAT as well as a legitimate open-source project called BOINC. BOINC, short for Berkeley Open Infrastructure Network Computing Client, is an open-source "Volunteer computing" platform maintained by the University of California with an aim to carry out "Large-scale distributed high-throughput computing" using participating home computers on which the app is installed.
The JavaScript downloader, in this case, activates two disjointed chains, one that leads to the deployment of a fileless variant of AsyncRAT and the other resulting in the BOINC installation.
The BOINC app, which is renamed as "SecurityHealthService.exe" or "Trustedinstaller.exe" to evade detection, sets persistence using a scheduled task by means of a PowerShell script.
The misuse of BOINC for malicious purposes hasn't gone unnoticed by the project maintainers, who are currently investigating the problem and finding a way to "Defeat this malware." Evidence of the abuse dates back to at least June 26, 2024.
"Infected clients actively connecting to malicious BOINC servers present a fairly high risk, as there's potential for a motivated threat actor to misuse this connection and execute any number of malicious commands or software on the host to further escalate privileges or move laterally through a network and compromise an entire domain."
"In the ongoing battle between security experts and threat actors, malware developers keep coming up with new tricks to hide their attacks," security researcher Moshe Marelus said.
News URL
https://thehackernews.com/2024/07/socgholish-malware-exploits-boinc.html
Related news
- EncryptHub Exploits Windows Zero-Day to Deploy Rhadamanthys and StealC Malware (source)
- Android Malware Exploits a Microsoft-Related Security Blind Spot to Avoid Detection (source)
- RESURGE Malware Exploits Ivanti Flaw with Rootkit and Web Shell Features (source)
- CERT-UA Reports Cyberattacks Targeting Ukrainian State Systems with WRECKSTEEL Malware (source)