Security News > 2024 > July > New Linux Variant of Play Ransomware Targeting VMWare ESXi Systems
Cybersecurity researchers have discovered a new Linux variant of a ransomware strain known as Play that's designed to target VMWare ESXi environments.
Manufacturing, professional services, construction, IT, retail, financial services, transportation, media, legal services, and real estate are some of the top industries affected by the Play ransomware during the time period.
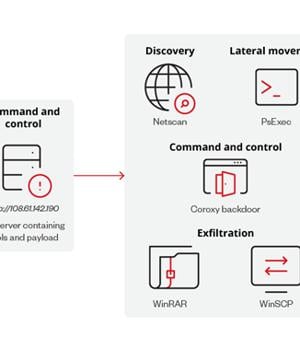
The cybersecurity firm's analysis of a Linux variant of Play comes from a RAR archive file hosted on an IP address, which also contains other tools identified as utilized in previous attacks such as PsExec, NetScan, WinSCP, WinRAR, and the Coroxy backdoor.
"Though no actual infection has been observed, the command-and-control server hosts the common tools that Play ransomware currently uses in its attacks," it said.
Further analysis has determined that the Play ransomware group is likely using the services and infrastructure peddled by Prolific Puma, which offers an illicit link-shortening service to other cybercriminals to help them evade detection while distributing malware.
The latest findings indicate a potential collaboration between two cybercriminal entities, suggesting that the Play ransomware actors are taking steps to bypass security protocols through Prolific Puma's services.
News URL
https://thehackernews.com/2024/07/new-linux-variant-of-play-ransomware.html
Related news
- New VanHelsing ransomware targets Windows, ARM, ESXi systems (source)
- Seven Malicious Go Packages Found Deploying Malware on Linux and macOS Systems (source)
- Over 37,000 VMware ESXi servers vulnerable to ongoing attacks (source)
- Chinese Hackers Target Linux Systems Using SNOWLIGHT Malware and VShell Tool (source)
- Rogue npm Packages Mimic Telegram Bot API to Plant SSH Backdoors on Linux Systems (source)