Security News > 2024 > April > Hackers Exploit Fortinet Flaw, Deploy ScreenConnect, Metasploit in New Campaign
2024-04-17 10:23
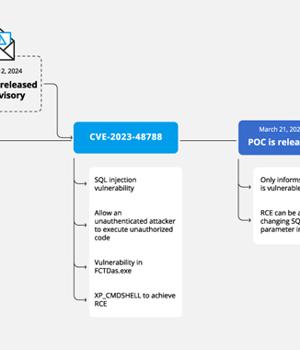
Cybersecurity researchers have discovered a new campaign that's exploiting a recently disclosed security flaw in Fortinet FortiClient EMS devices to deliver ScreenConnect and Metasploit Powerfun payloads. The activity entails the exploitation of CVE-2023-48788 (CVSS score: 9.3), a critical SQL injection flaw that could permit an unauthenticated attacker to execute unauthorized code or
News URL
https://thehackernews.com/2024/04/hackers-exploit-fortinet-flaw-deploy.html
Related news
- Russian Hackers Exploit Microsoft OAuth to Target Ukraine Allies via Signal and WhatsApp (source)
- Hackers Exploit Critical Craft CMS Flaws; Hundreds of Servers Likely Compromised (source)
- Hackers Exploit Samsung MagicINFO, GeoVision IoT Flaws to Deploy Mirai Botnet (source)
- Hackers exploit OttoKit WordPress plugin flaw to add admin accounts (source)
- Chinese Hackers Exploit SAP RCE Flaw CVE-2025-31324, Deploy Golang-Based SuperShell (source)
- Hackers exploit VMware ESXi, Microsoft SharePoint zero-days at Pwn2Own (source)
- Russian Hackers Exploit Email and VPN Vulnerabilities to Spy on Ukraine Aid Logistics (source)
- Chinese Hackers Exploit Ivanti EPMM Bugs in Global Enterprise Network Attacks (source)
- Chinese Hackers Exploit Trimble Cityworks Flaw to Infiltrate U.S. Government Networks (source)
- Mimo Hackers Exploit CVE-2025-32432 in Craft CMS to Deploy Cryptominer and Proxyware (source)
Related Vulnerability
| DATE | CVE | VULNERABILITY TITLE | RISK |
|---|---|---|---|
| 2024-03-12 | CVE-2023-48788 | Unspecified vulnerability in Fortinet Forticlient Enterprise Management Server A improper neutralization of special elements used in an sql command ('sql injection') in Fortinet FortiClientEMS version 7.2.0 through 7.2.2, FortiClientEMS 7.0.1 through 7.0.10 allows attacker to execute unauthorized code or commands via specially crafted packets. | 9.8 |