Security News > 2023 > September > 9 Alarming Vulnerabilities Uncovered in SEL's Power Management Products
Nine security flaws have been disclosed in electric power management products made by Schweitzer Engineering Laboratories.
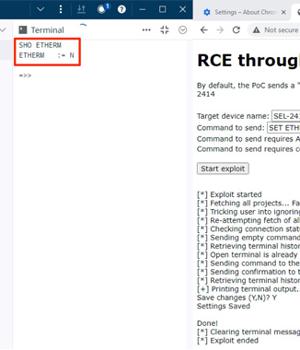
"The most severe of those nine vulnerabilities would allow a threat actor to facilitate remote code execution on an engineering workstation," Nozomi Networks said in a report published last week.
Exploitation of CVE-2023-31171 could be achieved by sending a phishing email that tricks a victim engineer into importing a specially crafted configuration file to achieve arbitrary code execution on the engineering workstation running the SEL software.
News of nine flaws adds to 19 security vulnerabilities previously reported in the SEL Real Time Automation Controller suite that could be exploited to "Obtain unauthorized access to the web interface, alter displayed information, manipulate its logic, perform man-in-the-middle attacks, or execute arbitrary code."
In July 2023, the operational technology security company also followed upon last years' findings, detecting five new vulnerabilities affecting the American Megatrends MegaRAC BMC software solution that could permit an attacker to achieve reset-resistant persistence and conceal a backdoor on the web-based BMC management interface.
14 more security bugs have been unearthed in the Phoenix Contact Web Panel 6121-WXPS, including four critical-severity flaws, that could be exploited by a remote attacker to completely compromise the appliances.
News URL
https://thehackernews.com/2023/09/9-alarming-vulnerabilities-uncovered-in.html
Related Vulnerability
| DATE | CVE | VULNERABILITY TITLE | RISK |
|---|---|---|---|
| 2023-08-31 | CVE-2023-31171 | SQL Injection vulnerability in Selinc Sel-5030 Acselerator Quickset 7.1.3.0 An Improper Neutralization of Special Elements used in an SQL Command ('SQL Injection') vulnerability in the Schweitzer Engineering Laboratories SEL-5030 acSELerator QuickSet Software could allow an attacker to embed instructions that could be executed by an authorized device operator. See Instruction Manual Appendix A and Appendix E dated 20230615 for more details. This issue affects SEL-5030 acSELerator QuickSet Software: through 7.1.3.0. | 6.5 |