Security News > 2023 > August > Chinese Hacking Group Exploits Barracuda Zero-Day to Target Government, Military, and Telecom
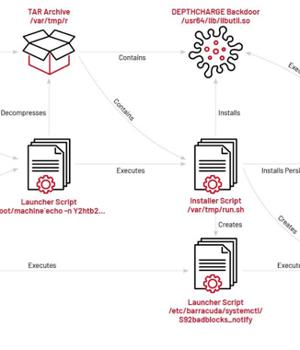
A suspected Chinese-nexus hacking group exploited a recently disclosed zero-day flaw in Barracuda Networks Email Security Gateway appliances to breach government, military, defense and aerospace, high-tech industry, and telecom sectors as part of a global espionage campaign.
What's more, FOXTROT shares overlaps with an open-source rootkit called Reptile, which has been extensively used by multiple Chinese hacking crews in recent months.
"FOXTROT and FOXGLOVE are also notable in that they are the only malware families observed being used by UNC4841 that were not specifically designed for Barracuda ESGs," Mandiant pointed out.
Another aspect that makes FOXGLOVE and FOXTROT stand out is the fact that they have been the most selectively deployed among all malware families used by UNC4841, exclusively using it to target government or government-related organizations.
UNC4841's Chinese connections are further bolstered by the infrastructure commonalities between the group and another uncategorized cluster codenamed UNC2286, which, in turn, shares overlaps with other Chinese espionage campaigns tracked as FamousSparrow and GhostEmperor.
"Shared infrastructure and techniques for anonymization are common amongst Chinese cyber espionage actors, as is shared tooling and likely malware development resources. It is likely that we will continue to observe Chinese cyber espionage operations targeting edge infrastructure with zero-day vulnerabilities and the deployment of malware customized to specific appliance ecosystems."
News URL
https://thehackernews.com/2023/08/chinese-hacking-group-exploits.html
Related news
- ⚡ Weekly Recap: iOS Zero-Days, 4Chan Breach, NTLM Exploits, WhatsApp Spyware & More (source)
- Craft CMS RCE exploit chain used in zero-day attacks to steal data (source)
- Enterprise tech dominates zero-day exploits with no signs of slowdown (source)
- Chinese Hackers Exploit SAP RCE Flaw CVE-2025-31324, Deploy Golang-Based SuperShell (source)
- ⚡ Weekly Recap: Zero-Day Exploits, Developer Malware, IoT Botnets, and AI-Powered Scams (source)
- Hackers exploit VMware ESXi, Microsoft SharePoint zero-days at Pwn2Own (source)
- ⚡ Weekly Recap: Zero-Day Exploits, Insider Threats, APT Targeting, Botnets and More (source)
- Mozilla fixes Firefox zero-days exploited at hacking contest (source)
- Chinese Hackers Exploit Ivanti EPMM Bugs in Global Enterprise Network Attacks (source)
- Chinese hackers breach US local governments using Cityworks zero-day (source)