Security News > 2023 > August > Lazarus Group Exploits Critical Zoho ManageEngine Flaw to Deploy Stealthy QuiteRAT Malware
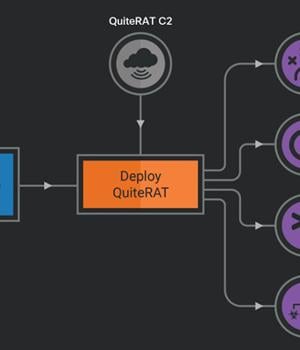
The North Korea-linked threat actor known as Lazarus Group has been observed exploiting a now-patched critical security flaw impacting Zoho ManageEngine ServiceDesk Plus to distribute a remote access trojan called such as QuiteRAT. Targets include internet backbone infrastructure and healthcare entities in Europe and the U.S., cybersecurity company Cisco Talos said in a two-part analysis published today.
What's more, a closer examination of the adversary's recycled attack infrastructure in its cyber assaults on enterprises has led to the discovery of a new threat dubbed CollectionRAT. The fact that the Lazarus Group continues to rely on the same tradecraft despite those components being well-documented over the years underscores the threat actor's confidence in their operations, Talos pointed out.
QuiteRAT is said to be a successor to MagicRAT, itself a follow-up to TigerRAT, while CollectionRAT appears to share overlaps with EarlyRAT, an implant written in PureBasic with capabilities to run commands on the endpoint.
"QuiteRAT has many of the same capabilities as Lazarus Group's better-known MagicRAT malware, but its file size is significantly smaller," security researchers Asheer Malhotra, Vitor Ventura, and Jungsoo An said.
The activity, detected in early 2023, involved the exploitation of CVE-2022-47966, a mere five days after proof-of-concept for the flaw emerged online, to directly deploy the QuiteRAT binary from a malicious URL. "QuiteRAT is clearly an evolution of MagicRAT," the researchers said.
"While MagicRAT is a bigger, bulkier malware family averaging around 18 MB in size, QuiteRAT is a much much smaller implementation, averaging around 4 to 5 MB in size."
News URL
https://thehackernews.com/2023/08/lazarus-group-exploits-critical-zoho.html
Related news
- EncryptHub Exploits Windows Zero-Day to Deploy Rhadamanthys and StealC Malware (source)
- Android Malware Exploits a Microsoft-Related Security Blind Spot to Avoid Detection (source)
- RESURGE Malware Exploits Ivanti Flaw with Rootkit and Web Shell Features (source)
- Lazarus Group Targets Job Seekers With ClickFix Tactic to Deploy GolangGhost Malware (source)
- Critical Ivanti Flaw Actively Exploited to Deploy TRAILBLAZE and BRUSHFIRE Malware (source)
- Critical Erlang/OTP SSH pre-auth RCE is 'Surprisingly Easy' to exploit, patch now (source)
- Critical Erlang/OTP SSH RCE bug now has public exploits, patch now (source)
- PoC exploit for critical Erlang/OTP SSH bug is public (CVE-2025-32433) (source)
- Docker Malware Exploits Teneo Web3 Node to Earn Crypto via Fake Heartbeat Signals (source)
- Hackers Exploit Critical Craft CMS Flaws; Hundreds of Servers Likely Compromised (source)
Related Vulnerability
| DATE | CVE | VULNERABILITY TITLE | RISK |
|---|---|---|---|
| 2023-01-18 | CVE-2022-47966 | Unspecified vulnerability in Zohocorp products Multiple Zoho ManageEngine on-premise products, such as ServiceDesk Plus through 14003, allow remote code execution due to use of Apache Santuario xmlsec (aka XML Security for Java) 1.4.1, because the xmlsec XSLT features, by design in that version, make the application responsible for certain security protections, and the ManageEngine applications did not provide those protections. | 9.8 |