Security News > 2023 > August > Russian Hackers Use Zulip Chat App for Covert C&C in Diplomatic Phishing Attacks
The phishing attacks feature PDF documents with diplomatic lures, some of which are disguised as coming from Germany, to deliver a variant of a malware called Duke, which has been attributed to APT29.
"The threat actor used Zulip - an open-source chat application - for command-and-control, to evade and hide its activities behind legitimate web traffic," Dutch cybersecurity company EclecticIQ said in an analysis last week.
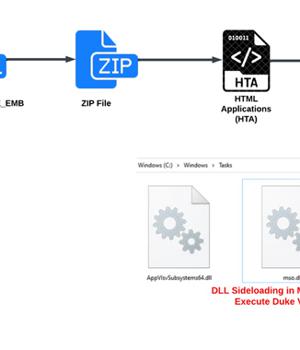
Should a potential target succumb to the phishing trap by opening the PDF file, a malicious HTML dropper called Invitation Farewell DE EMB is launched to execute JavaScript that drops a ZIP archive file, which, in turn, packs in an HTML Application file designed to deploy the Duke malware.
The development comes as the Computer Emergency Response Team of Ukraine warned of a new set of phishing attacks against state organizations of Ukraine using a Go-based open-source post-exploitation toolkit called Merlin.
"The capture of devices on the battlefield, their detailed examination, and the use of available access, and software became the primary vector for the initial access and malware distribution," the security agency said.
Some of the malware strains include NETD to ensure persistence, DROPBEAR to establish remote access, STL to gather data from the Starlink satellite system, DEBLIND to exfiltrate data, the Mirai botnet malware.
News URL
https://thehackernews.com/2023/08/russian-hackers-use-zulip-chat-app-for.html
Related news
- Microsoft: Russian-Linked Hackers Using 'Device Code Phishing' to Hijack Accounts (source)
- Microsoft: Hackers steal emails in device code phishing attacks (source)
- Hackers Exploit AWS Misconfigurations to Launch Phishing Attacks via SES and WorkMail (source)
- How to Prevent Phishing Attacks with Multi-Factor Authentication (source)
- Hacker pleads guilty to SIM swap attack on US SEC X account (source)
- Russian military hackers deploy malicious Windows activators in Ukraine (source)
- BadPilot network hacking campaign fuels Russian SandWorm attacks (source)
- whoAMI attacks give hackers code execution on Amazon EC2 instances (source)
- Chinese Hackers Exploit MAVInject.exe to Evade Detection in Targeted Cyber Attacks (source)
- Russian phishing campaigns exploit Signal's device-linking feature (source)