Security News > 2023 > July > Casbaneiro Banking Malware Goes Under the Radar with UAC Bypass Technique
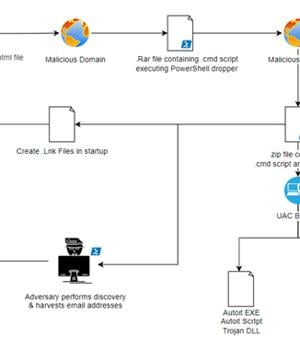
The financially motivated threat actors behind the Casbaneiro banking malware family have been observed making use of a User Account Control bypass technique to gain full administrative privileges on a machine, a sign that the threat actor is evolving their tactics to avoid detection and execute malicious code on compromised assets.
Casbaneiro, also known as Metamorfo and Ponteiro, is best known for its banking trojan, which first emerged in mass email spam campaigns targeting the Latin American financial sector in 2018.
Infection chains typically begin with a phishing email pointing to a booby-trapped attachment that, when launched, activates a series of steps that culminate in the deployment of the banking malware, alongside scripts that leverage living-off-the-land techniques to fingerprint the host and gather system metadata.
What's changed in recent attack waves is that the attack is kick-started by spear-phishing email embedded with a link to an HTML file that redirects the target to download a RAR file, a deviation from the use of malicious PDF attachments with a download link to a ZIP file.
Exe to achieve a UAC bypass and attain high integrity level execution.
"It is possible that the attacker deployed the mock folder to bypass AV detections or to leverage that folder for side-load DLLs with Microsoft-signed binaries for UAC bypass," the company said.
News URL
https://thehackernews.com/2023/07/casbaneiro-banking-malware-goes-under.html