Security News > 2023 > June > Iranian Hackers Using POWERSTAR Backdoor in Targeted Espionage Attacks
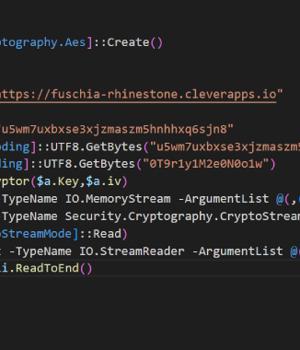
Charming Kitten, the nation-state actor affiliated with Iran's Islamic Revolutionary Guard Corps, has been attributed to a bespoke spear-phishing campaign that delivers an updated version of a fully-featured PowerShell backdoor called POWERSTAR. "There have been improved operational security measures placed in the malware to make it more difficult to analyze and collect intelligence," Volexity researchers Ankur Saini and Charlie Gardner said in a report published this week.
Recent intrusions orchestrated by Charming Kitten have made use of other implants such as PowerLess and BellaCiao, suggesting that the group is utilizing an array of espionage tools at its disposal to realize its strategic objectives.
Volexity, which detected a rudimentary variant of POWERSTAR in 2021 distributed by a malicious macro embedded in DOCM file, said the May 2023 attack wave leverages an LNK file inside a password-protected RAR file to download the backdoor from Backblaze, while also taking steps to hinder analysis.
"With POWERSTAR, Charming Kitten sought to limit the risk of exposing their malware to analysis and detection by delivering the decryption method separately from the initial code and never writing it to disk," the researchers said.
"The general phishing playbook used by Charming Kitten and the overall purpose of POWERSTAR remain consistent," the researchers said.
"The references to persistence mechanisms and executable payloads within the POWERSTAR Cleanup module strongly suggests a broader set of tools used by Charming Kitten to conduct malware-enabled espionage."
News URL
https://thehackernews.com/2023/06/iranian-hackers-charming-kitten-utilize.html
Related news
- Chinese Hackers Deploy MarsSnake Backdoor in Multi-Year Attack on Saudi Organization (source)
- North Korean hackers adopt ClickFix attacks to target crypto firms (source)
- Cisco warns of CSLU backdoor admin account used in attacks (source)
- Russian hackers attack Western military mission using malicious drive (source)
- Hackers Abuse Russian Bulletproof Host Proton66 for Global Attacks and Malware Delivery (source)
- Hackers abuse Zoom remote control feature for crypto-theft attacks (source)
- DPRK Hackers Steal $137M from TRON Users in Single-Day Phishing Attack (source)
- Lazarus hackers breach six companies in watering hole attacks (source)
- Chinese Hackers Abuse IPv6 SLAAC for AitM Attacks via Spellbinder Lateral Movement Tool (source)
- Iranian Hackers Maintain 2-Year Access to Middle East CNI via VPN Flaws and Malware (source)