Security News > 2023 > May > Microsoft, GitHub announce application security testing tools for Azure DevOps
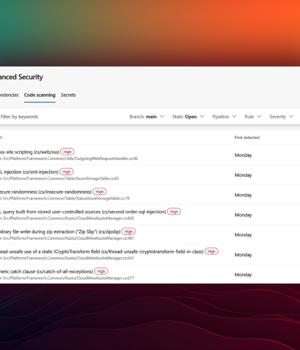
GitHub has announced that its application security testing tools are now more widely available for subscribers of Microsoft's Azure DevOps Services.
"GitHub Advanced Security for Azure DevOps can not only help you find secrets that have already been exposed in Azure Repos, but also help you prevent new exposures by blocking any pushes to Azure Repos that contain secrets," says Aaron Hallberg, Director of Product for Azure DevOps, Microsoft.
The tool identifies the open-source packages used in Azure Repos and the vulnerabilities in them, and advises users on how to upgrade those packages to mitigate vulnerabilities.
Developers can now run CodeQL scans directly from Azure Pipelines on code from Azure Repos and act on the results within the Azure DevOps environment.
"Issues detected in each of these categories are presented in a repository-scoped Advanced Security experience using the Azure DevOps design language," Hallberg noted.
GitHub Advanced Security for Azure DevOps has been in private preview since November 2022 and is now in public preview.
News URL
https://www.helpnetsecurity.com/2023/05/24/application-security-testing-devops/
Related news
- Microsoft Fixes 78 Flaws, 5 Zero-Days Exploited; CVSS 10 Bug Impacts Azure DevOps Server (source)
- Cryptojacking Campaign Exploits DevOps APIs Using Off-the-Shelf Tools from GitHub (source)
- Widespread Microsoft Entra lockouts tied to new security feature rollout (source)
- Microsoft Secures MSA Signing with Azure Confidential VMs Following Storm-0558 Breach (source)
- Security Tools Alone Don't Protect You — Control Effectiveness Does (source)
- Microsoft, Dutch security agencies lift veil on Laundry Bear cyber espionage group (source)