Security News > 2023 > May > China's Mustang Panda Hackers Exploit TP-Link Routers for Persistent Attacks
The Chinese nation-state actor known as Mustang Panda has been linked to a new set of sophisticated and targeted attacks aimed at European foreign affairs entities since January 2023.
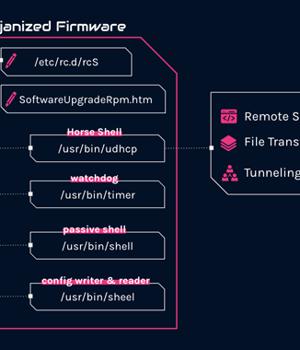
An analysis of these intrusions, per Check Point researchers Itay Cohen and Radoslaw Madej, has revealed a custom firmware implant designed explicitly for TP-Link routers.
The exact method used to deploy the tampered firmware images on the infected routers is currently unknown, as is its usage and involvement in actual attacks.
In an interesting twist, the router backdoor is believed to target arbitrary devices on residential and home networks, suggesting that the compromised routers are being co-opted into a mesh network with the goal of creating a "Chain of nodes between main infections and real command-and-control."
In relaying communications between infected routers by using a SOCKS tunnel, the idea is to introduce an additional layer of anonymity and conceal the final server, as each node in the chain contains information only about the nodes preceding and succeeding it.
In 2021, the National Cybersecurity Agency of France detailed an intrusion set orchestrated by APT31 that leveraged a piece of advanced malware known as Pakdoor to allow the infected routers to communicate with each other.
News URL
https://thehackernews.com/2023/05/chinas-mustang-panda-hackers-exploit-tp.html
Related news
- ⚡ THN Weekly Recap: Router Hacks, PyPI Attacks, New Ransomware Decryptor, and More (source)
- New ‘Rules File Backdoor’ Attack Lets Hackers Inject Malicious Code via AI Code Editors (source)
- Hackers Exploit Severe PHP Flaw to Deploy Quasar RAT and XMRig Miners (source)
- TechRepublic EXCLUSIVE: New Ransomware Attacks are Getting More Personal as Hackers ‘Apply Psychological Pressure” (source)
- Ongoing Cyber Attacks Exploit Critical Vulnerabilities in Cisco Smart Licensing Utility (source)
- Zero-Day Alert: Google Releases Chrome Patch for Exploit Used in Russian Espionage Attacks (source)
- Top 3 MS Office Exploits Hackers Use in 2025 – Stay Alert! (source)
- Hackers Repurpose RansomHub's EDRKillShifter in Medusa, BianLian, and Play Attacks (source)
- Chinese FamousSparrow hackers deploy upgraded malware in attacks (source)
- Hackers Exploit WordPress mu-Plugins to Inject Spam and Hijack Site Images (source)