Security News > 2023 > May > CLR SqlShell Malware Targets MS SQL Servers for Crypto Mining and Ransomware
Poorly managed Microsoft SQL servers are the target of a new campaign that's designed to propagate a category of malware called CLR SqlShell that ultimately facilitates the deployment of cryptocurrency miners and ransomware.
"Similar to web shell, which can be installed on web servers, SqlShell is a malware strain that supports various features after being installed on an MS SQL server, such as executing commands from threat actors and carrying out all sorts of malicious behavior," AhnLab Security Emergency response Center said in a report published last week.
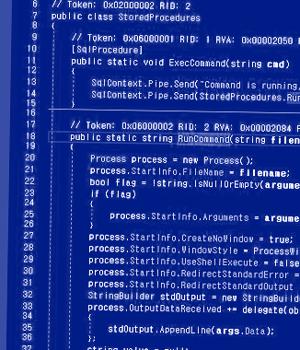
CLR stored procedures - available in SQL Server 2005 and later - refer to stored procedures that are written in a.NET language such as C# or Visual Basic.
The attack method discovered by the South Korean cybersecurity firm entails the use of CLR stored procedure to install the malware in MS SQL servers using the xp cmdshell command, which spawns a Windows command shell and passes an instruction as input for execution.
Some of the techniques employed by threat actors, including those associated with LemonDuck, MyKings, and Vollgar, concern the exploitation of internet-exposed MS SQL servers via brute-force and dictionary attacks to run xp cmdshell commands and OLE stored procedures and execute malware.
What's more, SqlShells named SqlHelper, CLRSQL, and CLR module have been used by different adversaries to escalate privileges on compromised servers and launch ransomware, proxyware, and incorporate capabilities to carry out reconnaissance efforts in targeted networks.
News URL
https://thehackernews.com/2023/05/clr-sqlshell-malware-targets-ms-sql.html
Related news
- Storm-1977 Hits Education Clouds with AzureChecker, Deploys 200+ Crypto Mining Containers (source)
- RedCurl cyberspies create ransomware to encrypt Hyper-V servers (source)
- New Crocodilus malware steals Android users’ crypto wallet keys (source)
- Over 1,500 PostgreSQL Servers Compromised in Fileless Cryptocurrency Mining Campaign (source)
- Outlaw Group Uses SSH Brute-Force to Deploy Cryptojacking Malware on Linux Servers (source)
- OPSEC Failure Exposes Coquettte’s Malware Campaigns on Bulletproof Hosting Servers (source)
- Police detains Smokeloader malware customers, seizes servers (source)
- Crypto Developers Targeted by Python Malware Disguised as Coding Challenges (source)
- Node.js Malware Campaign Targets Crypto Users with Fake Binance and TradingView Installers (source)
- Docker Malware Exploits Teneo Web3 Node to Earn Crypto via Fake Heartbeat Signals (source)